IT Pro Verdict
It's not perfect, but the Netgear ProSecure UTM150 provides comprehensive cover against the security threats faced by most small business networks, giving you the tools you need to manage both your users and the risk that comes with exposing your systems to the internet.

The Netgear ProSecure UTM150

Using the content blocking options you can easily prevent all or only certain users from viewing particular categories of con

By segmenting devices on the LAN into groups, by IP address, it’s easy to apply different settings to different users, or gro

The UTM handles https communications by inserting itself between the secure site and the client on your network, checking whe
The Netgear UTM 150 is a unified threat management device: an internet gateway, with a built-in stateful firewall and subscription web and email filtering. It sits between your broadband connection, or connections, and the internal network.
Set up is instantaneous; simply plug in your broadband device. The UTM150 has four WAN ports: so if one internet connection goes down, it switches immediately to a backup. Alternatively, you can configure it to load balance across all available bandwidth, helping to get the highest speeds and best return on investment from your broadband.
The firewall's basic configuration is to allow all outgoing connections, but only let incoming connections that have been requested by a client behind the firewall. You can easily customise this using the web interface, allowing or blocking specific services. We tried blocking and allowing a range of services, for the whole network, for certain device groups on the network and by schedule with perfect results every time.
Web- and email- and spam-filtering only works when you subscribe to the online filter services bundled with the product. A year's free subscription is included with the UTM, after that you pay $1062 (approximately 660) for a 1-year account and $2710 (approximately 1,685) for a 3-year account.
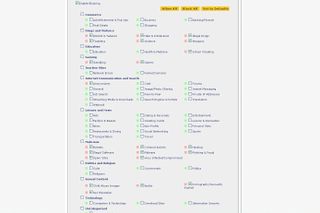
Content filtering worked well, but sometimes threw up false positives. It's easy enough to remedy using whitelists though.
URL filtering worked all the time, without any exception. Content filtering worked well, but sometimes threw up false positives. For instance, it classified an online human resources booking system as a "computers and technology" site, which was therefore blocked under the filtering scheme we had set up. Overall, however, the number of false positives was low, and it's easy to put a site on a whitelist if you want to make an exception for it but still keep your general rule.
Email antivirus filtering efficiently stripped out .exe and other suspicious files, as we'd specified, and scanned all outgoing messages without noticeably delaying their being sent. We did, however, have to remove the [MALWARE FREE] notice that the device, by default, adds to all outgoing mails it scans.