Attackers target vulnerability in Cisco switches
'Nation-state' actors leave political messages on 168,000 unpatched IoT devices

Attackers are exploiting a vulnerability in Cisco switches deployed in data centres across the world to leave politically-motivated messages, according to researchers.
Although the scale of the attack has yet to be determined, Talos, Cisco's cybersecurity arm, has identified more than 168,000 IoT devices with the vulnerability, with analysis by Kaspersky Lab suggesting the attack is mostly targeting the Russian-speaking portion of the internet, impacting entire internet providers and data centres.
A bot is searching for vulnerable Cisco switches via the Internet of Things (IoT) search engine Shodan, according to Kaspersky, and once it finds a vulnerability, can exploit the Cisco Smart Install Client software.
The flaw allows attackers to run arbitrary code on the vulnerable switches, before they are able to rewrite the Cisco IOS image and change the configuration file. Devices then boot up with the message "don't mess with our elections" and an image of the United States flag, before the switch becomes unavailable.
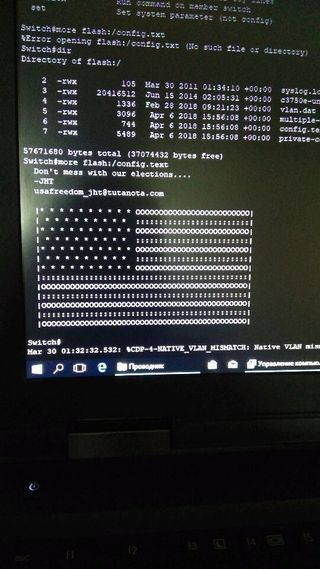
Image credit: Kaspersky
Cisco Talos threat researcher Nick Biasini warned that network administrators need to be especially vigilant, suggesting the simplest way to mitigate these issues is to run the command novstack on the affected device.
He said: "It can be easy to 'set and forget' these devices, as they are typically highly stable and rarely changed. Combine this with the advantages that an attacker has when controlling a network device, and routers and switches become very tempting targets."
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
Cisco has strongly recommended all customers review their architecture, and use tools provided by Talos to scan their network and remove Cisco Smart Install Client from all devices in instances where it's not being used.
While Talos believes attackers are "associated with nation-state actors", screenshots posted on Twitter by one affected user indicates a group named 'JHT' has claimed responsibility.
Reuters, meanwhile, reported a statement from the Iranian Communication and Information Technology Ministry that says the attack has affected 3,500 switches in Iran.
The Smart Client vulnerability dates back to February of last year, where Cisco first became aware of a significant increase in scans attempting to detect devices where the Smart Install feature remained enabled and without proper security controls, after setup was completed.
Smart Install was initially designed to make life easier for system administrators by allowing remote configuration and OS image management on Cisco switches. By design, these do not require authentication.
Kaspersky Labs suggests it may be a problem of data centres that fail to limit access to the TCP 4786 port, which needs to be open for the Smart Install to work, or to disable Smart Install once it is no longer in use.
Picture credit: Bigstock

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.




