Breach site finds 1 billion accounts in hacked datasets
The databases contain email and password pairs from various past data breaches

The security conscious among you will be acutely aware of the dangers of password reuse, but the discovery of over 1 billion emails and passwords for sale on the dark web, some of which is more than 10 years old, has highlighted not only the scale of the problem, but the issue of retrofitting passwords.
Breach notification service Have I Been Pwned? (HIBP) has discovered troves of user credentials either being sold on hacking websites, or publicly available on data hosting websites.
This hacked data was found in two separate "combo lists" - collections of email addresses and associated passwords that have been scalped from various data breaches and leaks. It is thought that these lists were created as recently as late 2016.
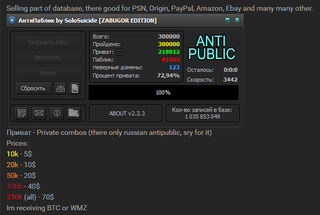
One list, known as the "Anti Public Combo List", contains 457,962,538 distinct email addresses, and although HIBP creator Troy Hunt, who first reported the discovery of the lists last Friday, has so far been unable to trace the source of the data, he believes it comes from multiple breaches rather than a single event.
Of HIBP's 1.1 million subscribers, who are notified if their email appears in a breach, more than 130,000 were found inside the Anti Public list, Hunt explained.
"I grabbed a handful of the ones who'd most recently signed up to the service and fired them off an email," said Hunt. "It was essentially 'hey, I've found your data online, can you help me verify if the password on file for you is correct'.
"I didn't know the site it originally came from nor did I have anything like their physical or IP address. But people were wiling to help regardless and I got a steady flow of confirmations."
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
It wasn't until the discovery of a second list, known as Exploit.In, that the full scale of the collection came to light. This list in particular caught Hunt's eye as it happened to include a familiar address:
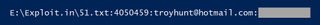
"Dammit! This is indeed my email address and the password is indeed one I recall carelessly throwing at a bunch of forums back in the noughties somewhere," Hunt wrote.
This second list comes in at just over 24GB in size, holding a mass of email address and password pairs - a total of 593,427,119 unique addresses. What's more, only 222 million of these were also found in the Anti Public list, meaning 63% of the Exploit.In records were unique.
Some of these breached services are still active
Although it has been almost impossible to determine any sources of the data, Hunt explained to IT Pro that many of these services will still be active. What is concerning is that although many users were able to confirm the data was accurate, they also admitted they were heavily reused as standard account passwords, including on accounts that were more than likely forgotten about.
"My own data almost certainly came from a car forum I used to frequent and that's definitely still running," said Hunt. "But even if these services weren't (active), the mere presence of credentials that are reused across other services is what poses the risk."
What is also particularly concerning is that this list is currently sitting on a publicly accessible Russian file-hosting site, and copies have almost certainly been made.
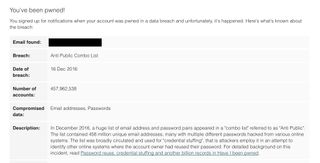
My own email address was among those found in the database
The two lists alone amount to 1,051,389,657 unique entries - increasing the size of the entire HBIP data set by almost 40%. Hunt has even said that the site's current subscription to Microsoft Azure will need to be expanded to host all that extra data.
Black market data sales
'Combo lists' of this kind are often sold on black market websites, which spike in activity around the time of a major hack. In the case of the Anti Public list, 'private combos' were also found, offering tiered prices for email and password pairs, as little as $5 for 10,000; up to $70 for 210,000.
Buyers will then take this data and attempt to break into accounts on "totally unrelated websites", according to Hunt. Often passwords are 'hashed' with very flimsy layers of protection, which once cracked offer plain text passwords. These are then loaded into an automated hacking tool that pumps email address and password combos into a website until it scores a hit, known as 'credential stuffing'.
This is an incredibly efficient method - there are many cheap, premade tools for hire on the web, and for the targeted site, it is almost impossible to prevent.
The best thing we can do to prevent these lists is use a password manager. These tools are able to generate unique passwords for websites and forms, auto-filling fields from a vault stored in the cloud - effectively neutering the potential danger of a leaked data set.
"As fallible humans, we reuse passwords," Hunt said. "We've all done it at one time or another and whilst I hope that by virtue of you being here reading security stuff you've got yourself a good password manager, we've all got skeletons in our closets."
The full report can be read here.
Body copy pictures courtesy of Troy Hunt (blog)
WATCH: Learn more about the security threats facing businesses today and how to combat them in this free webinar WATCH NOW
Dale Walker is the Managing Editor of ITPro, and its sibling sites CloudPro and ChannelPro. Dale has a keen interest in IT regulations, data protection, and cyber security. He spent a number of years reporting for ITPro from numerous domestic and international events, including IBM, Red Hat, Google, and has been a regular reporter for Microsoft's various yearly showcases, including Ignite.





