Researchers warn against 'hackable' robots
Security firm claims factory and home robots could spy on or attack people
Cyber security firm IOActive claims it has discovered flaws in several commercially available robots that could lead to the devices hacking networks or even physically attacking their owners.
The company investigated well-known robots such as Pepper and NAO, as well as other robots from SoftBank, Universal and UBTech, disclosing the vulnerabilities to the companies back in January. The full reports one for each company are only being made available now, however, as IOActive waited for the companies to create patches for the devices, in accordance with its responsible disclosure policy.
Robot voyeurs, robot spies
IOActive found that SoftBank's Pepper and NAO robots, both of which are domestic robots aimed at children, could be used by hackers to capture video and audio.
The vulnerability lies in IOActive's claim that, by default, NAOqi OS the robots' operating system is in development mode, leaving all ports open on all network interfaces. Once an attacker has access to the system, they can access an object called ALProxy, which allows the creation of a proxy to any NAOiq module with no authorisation check. This then means the attackers can make calls to processes including ALVideoDevice and ALPeoplePerception, said the security firm.
"The following call retrieves the remote robot camera content from the ALVideoDevice video source and returns a pointer to the locked ALImage, with data array pointing directly to raw data," the researchers claim in their paper.
"This weakness can lead to the exposure of resources or functionality to unintended actors, providing attackers with sensitive information and even execute arbitrary code. Other modules [such] as ALPeoplePerception can be used to extract information of tracked people around the robot and obtain basic information about them. This module gathers visual information from RGB cameras and a 3D sensor if available. All new people detected in the current video frame are associated (when possible) with previously known people."
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
SoftBank's EMEA PR manager Vincent Samuels told IT Pro: "This report does not highlight new vulnerabilities. We had already identified old ones before the first report by IOActive was released last March and fixed them since."
Similarly, UBTech's Alpha robots small humanoid robots also aimed at children and the associated app don't encrypt data before it's sent back to the central server, IOActive said, meaning potentially sensitive information could be intercepted while it's transmitted in the clear.
"The Alpha 2 android application does not verify any cryptographic signature when downloading and installing the APK apps into the mobile device," the researchers said.
"Furthermore, due to 'App-to-Server Missing Encryption' it is possible to perform a man-in-the-middle attack in order to change the APK URL and install a customized malware on the device or the robot."
Robot assassins
There's an even more sinister element to the vulnerabilities IOActive said it found in SoftBank's robots, as well as those of industrial robot arm creator, Universal Robots: they can be programmed to maim the humans around them.
In Universal's UR3, UR5 and UR10 models, there are a number of problems with authentication when accessing the robots from inside the network they're attached to, IOActive said - namely that there are no authentication procedures.
Should an attacker gain access to the network they're connected to, they could theoretically cause the robot arm to move around at random, the security company explained, which could cause injury to any nearby humans.
Meanwhile, Rethink Robotics' Baxter and Sawyer robots are allegedly open to attacks via their SDK, also due to a problem with a lack of authentication. These robots can move around a factory floor autonomously but if accessed by a hacker, their collision avoidance systems could be turned off, leading them to run into each other or the humans sharing their environment.
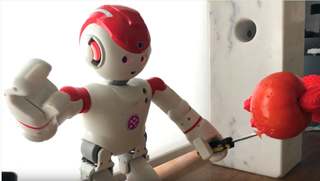
The domestic robots aren't invulnerable to this kind of attack either, as demonstrated in the video of UBTech's robot below.
John Rhee, general manager for North America at UBTech, said: "UBTech has been made aware of a sensationalistic video produced by IOActive featuring the Alpha 2. The video is an exaggerated depiction of Alpha 2's open-source platform. UBTech encourages its developer community to code responsibly and discourages inappropriate robot behaviour."
A real threat
This is far from the first time connected devices aimed at children have been found to be vulnerable to hacking, however. In 2015 Hello Barbie, a connected Barbie doll, was found to have a vulnerability that could lead to its microphone being remotely accessed by potentially malicious actors. Following that incident, the security researcher who discovered the flaw said parents should be wary of all connected toys.
Independent security researcher Graham Cluley told IT Pro: "Time and time again we hear about connected toys and other IoT devices which are putting our privacy at risk because of manufacturers who have clearly not even considered security, let alone treated it as a priority. It doesn't matter if we haven't heard of real-life exploitation of these flaws or not, the fact that they exist at all is problem enough."
"Manufacturers need to learn that simply 'sellotaping the internet' onto a device to make it easier to market isn't the right approach," he added. "If you are going to make a connected toy you should always put effort into ensuring that it is secure, and consider how you will easily update devices if a flaw is found after the product is released."
IT Pro has contacted all the manufacturers covered by the reports, but hadn't received a response from some of them at the time of publication.
Rhee added: "UBTech is committed to maintaining the highest security standards in all of it's products. As a result the company has conducted a full investigation into the claims made in the IOActive report regarding the Alpha 2 robot. The Alpha 2 robot was designed to be on an open-sourced platform where developers are encouraged to program their robots with code. UBTech has fully addressed any concerns raised by IoActive that do not limit our developers from programming their Alpha 2."
Main image credit: IOActive
This story was originally published on 22 August 2017, and updated on 23 August with comment from UBTech and SoftBank

Jane McCallion is ITPro's deputy editor, specializing in cloud computing, cyber security, data centers and enterprise IT infrastructure. Before becoming Deputy Editor, she held the role of Features Editor, managing a pool of freelance and internal writers, while continuing to specialise in enterprise IT infrastructure, and business strategy.
Prior to joining ITPro, Jane was a freelance business journalist writing as both Jane McCallion and Jane Bordenave for titles such as European CEO, World Finance, and Business Excellence Magazine.




