Code used to hack BA passenger data discovered
A cyber security firm has found the script used to steal the airline's customer data

It took just 22 lines of JavaScript to steal the data of hundreds of thousands of British Airways (BA) passengers, according to the cyber security firm that says it has found the code.
Last week, the airline revealed it had been the subject of a data breach thought to have affected around 380,000 customers over a two-week period back between late August and early September. The stolen information included personal and payment information taken from BA's website and mobile app.
Looking into the breach, cyber security firm RiskIQ has claimed that a fraudulent group called Magecart could be behind it, citing its involvement with the recent breach to Ticketmaster as an example of its modus operandi.
"Magecart injects scripts designed to steal sensitive data that consumers enter into online payment forms on e-commerce websites directly or through compromised third-party suppliers used by these sites," said RiskIQ threat researcher Yonathan Klijnsma.
"Recently, Magecart operatives placed one of these digital skimmers on Ticketmaster websites through the compromise of a third-party functionality resulting in a high-profile breach of Ticketmaster customer data. Based on recent evidence, Magecart has now set their sights on British Airways, the largest airline in the UK."
A technique called skimming was used in both breaches. Skimmers are traditionally used by criminals on credit cards in the form of devices hidden within credit card readers on ATMs, fuel pumps, and other machines people use for day-to-day purchases that steal payment data for a criminal to either use or sell to a third party.
However, for the BA breach, Magecart customised a skimmer and embedded it into the airline's website which runs on JavaScript. RiskIQ posted a picture of a cleaned up version of the script that it said as very simple but effective'.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
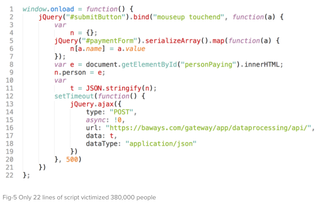
According to RiskIQ, mouseup' and touchend', are events for when someone lets go of the mouse after clicking on a button or when someone using a touchscreen device lets go of the screen after pushing a button. This means that once a user hits the button to submit their payment on the compromised British Airways site, the information from the payment form can be extracted and sent to the attacker's server.
This particular type of skimmer is very much attuned to how BA's payment page is set up, according to RiskIQ, which suggests the hackers had carefully considered how to target the airline instead of blindly injecting a regular Magecart skimmer.
Image: RiskIQ
Bobby Hellard is ITPro's Reviews Editor and has worked on CloudPro and ChannelPro since 2018. In his time at ITPro, Bobby has covered stories for all the major technology companies, such as Apple, Microsoft, Amazon and Facebook, and regularly attends industry-leading events such as AWS Re:Invent and Google Cloud Next.
Bobby mainly covers hardware reviews, but you will also recognize him as the face of many of our video reviews of laptops and smartphones.





