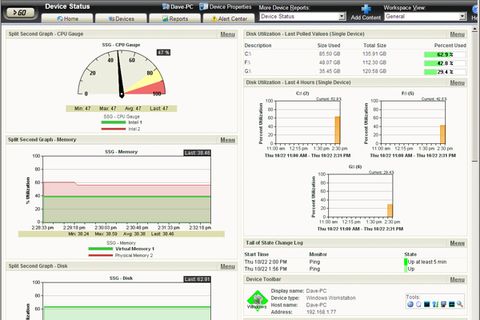
IT Pro Verdict
Despite the sheer range of features in v14, Ipswitch has done a good job in keeping them easily accessible. The device discovery routine is even smarter than before, although it’s about time Ipswitch simplified custom dynamic group creation, as this still something of a pain point. Even so, if you want full network device and application monitoring, along with sophisticated alerts, then the Premium edition is well worth the outlay.
WhatsUp Gold has always been Ipswitch's flagship product and this latest version (v14) of its network monitoring software manages to pack in even more new features.

Originally focusing on providing SMBs with an affordable monitoring solution, the previous two versions gradually fed in extra goodies with the aim of increasing its appeal to larger businesses and enterprises.
The new Welcome Centre greets you and provides quick access to the WhatsUp Gold Assistant.
Ipswitch still offers the standard version as an affordable option for SMBs looking for device discovery, mapping, monitoring, alerting and reporting. The Premium Edition on review adds support for WMI to deliver application as well as device monitoring. This enables you to configure monitors for apps including SQL Server and Exchange and automate actions such as restarting failed services.
Installation is a swift affair, and on loading the main program you'll meet the first new feature in v14. The Welcome Centre provides a tour of the key features, links to the WhatsUp Gold community and, more importantly, access to the new Assistant.
The Assistant makes light work of device discovery and offers a number of methods for scanning your network. After providing the IP address of an SNMP enabled router and a read community name you can use SmartScan, which queries each device's SNMP MIB. Alternatively, you can scan an IP address range and a Windows network or import a hosts file.
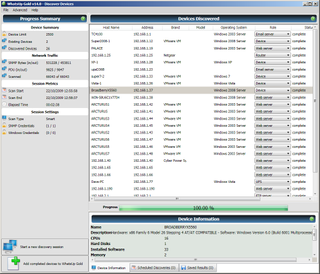
The improved Discovery routine made a good job of identifying the lab's servers, workstations and network devices.
It made a fairly decent stab at identifying the systems on our network and got very few wrong. We had one Windows Vista system with an APC UPS attached via USB and for some reason the scan identified the system itself as a UPS. We could change the properties of this system but were surprised to find no entry for a Windows Vista workstation.
However, the scan successfully spotted that a large number of our test clients were VMs on two VMware ESX Server 4 systems and it also saw that some of them were running Windows 7 as well as XP, Server 2003 and Server 2008.
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.