We created our own list of patterns and keywords and tested it by trying to send Word documents using FTP and SMTP. It worked perfectly as files that didn't have a match were allowed through and all those that did were blocked.
You can also apply auditing and shadowing policies to NetworkLock. With this activated we could see all activities from the console, view all emails being sent and see the subject line and the message content along with attachments and their contents.
ContentLock adds an extra dimension to NetworkLock - instead of a wholesale application block you could permit access but decide what files can and can't be transmitted. ContentLock also applies to removable devices so you can allow users to copy only some files to USB sticks, blocking more sensitive information.
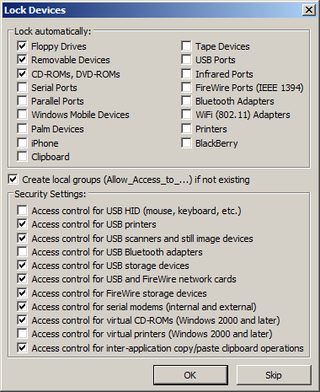
DeviceLock can manage access to every conceivable workstation port and removable storage device.
DeviceLock 7 has an extensive range of controls for protecting business data and stopping insider theft. The optional features add considerably to the price and it's long overdue for for a centralised management console but it does cover all exits from the network and provides essential logging and auditing facilities.
Verdict
DeviceLock provides some of the best controls for ensuring that sensitive data doesn’t get into the wrong hands. The new NetworkLock and ContentLock options are well worth considering as they add extra levels of security for protocols and applications but they are expensive for SMBs. We also think it’s about time DeviceLock simplified management by amalgamating all the different consoles into just one which would make it easier to use.
RAM: 64MB Hard disk space: 25MB Operating system: Windows NT or later Options: For 100-199 seats; NetworkLock £14 per seat; ContentLock £28 per seat (all ex VAT)
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.

