For anti-virus policies, you can decide how infected files are handled, create schedules for full systems scans and set up email alerts. Live protection can be enabled so if ESDP can't identify a suspicious file from the local signature files it'll pop online and check it against Sophos' hosted database service.
ESDP had no problems when we introduced some genuine viruses to our endpoints as these were blocked and placed in a local quarantine area. The agent notified the console each time which then flagged up a virus alert within a few seconds.
Application control policies are as easy to use and Sophos includes a heap of predefined applications which is just as well as you can't add your own. We were able to block access to utilities such as FTP clients, email apps including Windows Mail and Outlook Express and various browsers, although for Microsoft Office you can only block the entire suite.
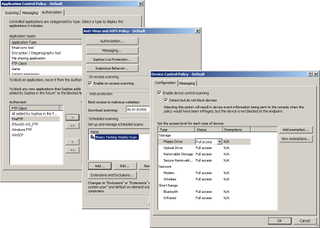
Policies are used for each ESDP component and allow you to control the anti-virus scanner, application usage and access to removable storage.
ESDP's device control isn't a patch on DeviceLock as it can only control access to floppy, optical and USB removable storage plus modems, wireless and Bluetooth devices. However, you can passively monitor and log usage on each endpoint, block access entirely or allow read-only or full access. With a policy set to block all usage we inserted USB sticks on some of our endpoints and received pop up warnings advising us that access wasn't permitted.
Data control policies allow you to apply file matching rules to stop them being copied or emailed. File contents can also be checked for keywords, phrases and patterns and Sophos provides a huge predefined list of patterns which includes those required for compliancy with HIPAA, PCI-DSS and PII standards.
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.

