IT Pro Verdict
Businesses that have standardised on Microsoft Outlook in the workplace will find TITUS Aware a simple and cost effective method of preventing data leaks. By actively involving users and helping them resolve policy breaches it can reduce support overheads and will also educate them about their responsibilities in protecting confidential information.

TITUS Aware logo

The Administration Tool is where all policies are defined and you can apply an extensive range of content checks to users’ em

The Global Options are used to activate features for the TA Outlook agent and control how it behaves.

Policy groups are used to validate recipients and mail domains as well as actual message and attachment content.

Users can classify messages from the Outlook Ribbon and if they infringe a policy plenty of remediation assistance is provide

Wizards help resolve message issues and the TA’s redaction feature can blot out unacceptable words.
Email data leakage is a constant worry for businesses but TITUS Aware (TA) takes a refreshingly new approach to this problem. Instead of rigidly enforcing DLP (data leakage prevention) policies it engages Microsoft Outlook users in the process of reviewing their emails and rectifying those that violate security policies.

We found TA simple enough to deploy as you install a small MSI package on each client system which can be done manually or via an AD Group Policy. TA supports all versions of Outlook from 2003 upwards. For testing in the lab we used Windows 7 systems running Outlook 2007.
The only other requirement on each client is a couple of registry modifications to point it at the location of the TA policy files. We manually edited our clients' registries, but this can also be done via Group Policies for larger user bases.
An Administration Tool is provided to create and manage all policies. Each policy uses a proprietary file which contains settings that determine how the TA client component should behave and links to sets of XML content validation files.
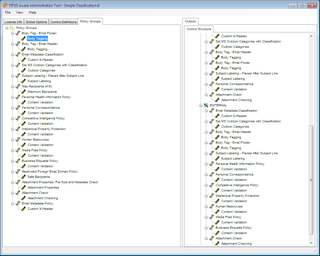
The Administration Tool is where all policies are defined and you can apply an extensive range of content checks to users' emails.
All the control and XML files can be stored in a central location on the network. They are then tied to each client by their respective registry entries. This allows a variety of policies to be assigned to different groups and XML files can be shared where a base set of content validation checks is applied to multiple groups.
The XML files store a specific set of content validation criteria which makes TA very versatile. You can use them to store lists of restricted external mail domains and countries, permitted mail domains, attachment controls and mail content checks.
TA offers a good range of controls over mail attachments as it can apply size restrictions and only allow certain file types to be sent. More importantly, it can scan the message subject and body plus the contents of attachments looking for keywords and phrases.
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
