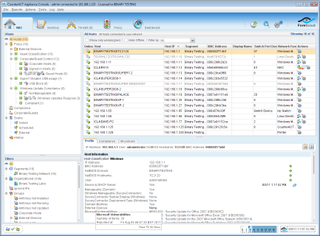
The CounterACT Console is well designed and provides high levels of information about monitored systems and policy status.
The appliance then starts identifying all devices on the network and automatically populating the console with their details. The scanning process uses the open source Nmap utility and is swift as after only a few minutes CounterACT had listed all our Windows Server 2003 and 2008 systems, Windows XP, Vista and 7 clients and other network devices including firewalls, printers and even NAS appliances.
The interface is well designed with a left pane showing all discovered devices plus policies and their status. The pane below allows views to be filtered where you place hosts with common attributes in groups and apply NAC policies to them.
Predefined policies are provided to get you out of the starting blocks, but it's easy enough to create your own. A classification policy places all new systems in the correct group so, for example, any that haven't authenticated to a recognized server can be classed as guests where they will have the appropriate policy applied.
Rather than block access completely, the policies can provide self-service and remediation services to guest users. You can present them with a web login page and the details they enter will be checked against selected authentication servers.
Guest network access can be configured automatically by using an ACL (access control list) or by placing the user in a separate VLAN. If a system pops up that you really don't want on the network, the policy can interact with a network switch and disable the port the system was seen on. Alternatively, you can apply the virtual firewall and use rules in the policy that determine what it can communicate with.
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.

