The BungeeAir Power Wireless Security Tether fob is powered by two long-lasting watch batteries, but the case doesn't draw power from the iPhone itself it has a built-in battery of its own.
This does make the case rather bulky at its bottom end and it adds 70g to its weight, but it does serve a handy extra purpose - press the button on its back and it packs sufficient juice to recharge an empty iPhone battery by about 50 per cent.

Kensington provides a free app (via the iTunes App Store) for configuring the wireless tether and this includes a short video to explain its operation, but set-up is sufficiently simple to make this unnecessary.
Simple app-based configuration
The app has a simple arm/disarm' toggle for setting the proximity alarm, but this must be set in conjunction with the physical activation switch on the fob. There's also a "Find my key" option that manually triggers the fob's alert, which is useful for people who tend to lose their keys more often than their smartphone.
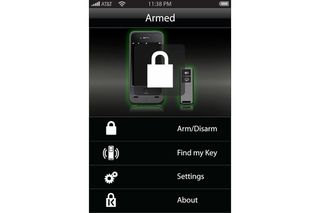
Conversely, the fob also has a button that manually triggers the app's alert, which is useful for finding an iPhone when it isn't where you thought it was. Both the fob and app will also sound an alert if someone tries to remove the BungeeAir Power Wireless Security Tether case, while a silence' switch on the fob is handy when nipping out of tether range for a moment although leaving the iPhone unattended and unsecured defeats the object somewhat.
Jennifer Scott is a former freelance journalist and currently political reporter for Sky News. She has a varied writing history, having started her career at Dennis Publishing, working in various roles across its business technology titles, including ITPro. Jennifer has specialised in a number of areas over the years and has produced a wealth of content for ITPro, focusing largely on data storage, networking, cloud computing, and telecommunications.
Most recently Jennifer has turned her skills to the political sphere and broadcast journalism, where she has worked for the BBC as a political reporter, before moving to Sky News.

