All further configuration is via the appliance's web interface, which opens with an informative status screen showing tables and graphs of hourly and daily inbound and outbound mail traffic. It's all colour-coded, so it's easy to see what mail is being allowed, blocked, tagged or quarantined.
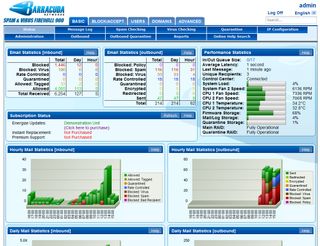
Barracuda's web interface provides easy access to all security features and opens with a detailed graphical overview of inbound and outbound message activity.
Next, mail recipient domains and the addresses of the mail servers the appliance will be routing mail for are added. Incoming mail must also be routed to the appliance and this can be achieved with a firewall port-forwarding rule, or by changing the DNS MX record.
For inbound mail, Barracuda uses an impressive arsenal of spam detection tools which include Bayesian algorithms, real-time blacklists, reverse DNS lookups, IP reputation analysis, fingerprinting, content filtering, keyword blocking and intent analysis. These are used to derive a score for each message and determine whether suspect messages are blocked, quarantined or tagged.
The Energize Update subscription seems high, but this does also include free access to Barracuda's Cloud Protection Layer (CPL). This can reduce local traffic by applying pre-filters to incoming mail, so spam and mail-borne viruses are stopped before they even get to the local network.
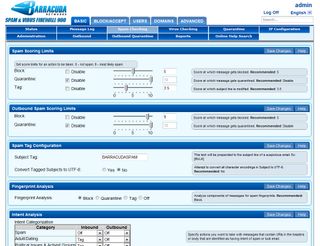
You can tweak the spam detection scoring system but we found it worked very well on the default values.
Rather than use bogus or old samples of harvested spam to test detection rates, we opted to set up the appliance to scan incoming mail in a totally live environment. This is a far more realistic test of the appliance's detection techniques, since it has to handle new and emerging threats in real time.
We left the spam scores and actions at their default settings and configured our Outlook clients to move any tagged messages into a separate folder. The appliance's message log was monitored during the test and, on completion, was exported into a spreadsheet for further analysis.
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.

