IT Pro Verdict
A good-value online backup and storage service which has been designed with business in mind. We like the simple interface as well as the logging and reporting tools.

Egnyte Hybridcloud

Egnyte Hybridcloud - Interface

Egnyte - Uploading

Egnyte - Permissions
Unlike the multitude of cloud-storage services such as Dropbox, Egnyte is specifically designed for business. We take a look at the key features to see if this is suitable for use within the enterprise.
Permissions and security
Egnyte aims to provide tight security. Data transfers, including automated backups, are protected with 256-bit AES encryption over SSL. By default, only authenticated users who provide their login credentials can access a shared folder.
The service allows you to create user logins from the web interface. Though the first time a new user logs in they will be forced to change their admin-assigned password. It is possible to create a folder available without protection: handy if you want to quickly share files with a third party. Access can also be revoke after sharing.
Permissions available are read-only, read-write and read-write-delete so admins can configure this as appropriate. If things get complicated you can put your users into groups and assign permissions to the groups, allowing you to work more quickly.
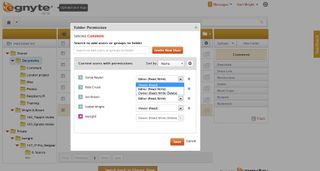
With Egnyte, you can specify each user's permissions folder by folder, so they can be shared without compromising your security policies
A good report
Egnyte has introduced a user login report. This records who logged in to the system and the IP address they used. As an administrator, you also get notified by a message to your inbox when users whose accounts you created log in for the first time.
Egnyte can also generate a range of other reports: allowing you to audit user permissions, the status of cloud-synced backups and folder sizes. Reports are easy to run, it takes just one or two clicks, and you can export them to Excel.