IT Pro Verdict
The XTM 26-W can be tricky to configure but it delivers a range of features at an affordable price for SMBs. Its security policies are versatile and WatchGuard’s application awareness can strictly control social networking in the workplace.
In this exclusive review, we look at the new XTM 26-W which brings together a host of security features and adds 11n wireless plus rogue AP detection to the mix. This model represents the top of the XTM 2 family tree and claims a 540Mbits/sec firewall throughput and 75Mbits/sec with all UTM functions enabled.
The price we've shown is for the one-year Security Bundle. Along with WatchGuard's LiveSecurity updates and support, this activates IPS, web content filtering, anti-spam, anti-virus, application controls, HTTPS inspection and WatchGuard's own reputation enabled defence.
You can cut costs by starting with the XTM 25-W whichcosts 595 for the same one-year bundle. The only difference is its license restricts firewall and UTM throughputs to 240Mbits/sec and 35Mbits/sec respectively. If you need more bandwidth you will need to purchase a software feature key which turns it into an XTM 26-W.

Along with a dual band wireless AP, the XTM 26-W has five Gigabit network ports
Deployment
There are a range of deployment options with mixed-mode routing the most flexible as it allows each of the appliance's five Gigabit ports to be defined as separate interfaces. We opted for this mode and had the appliance up and running in a few minutes thanks to a wizard based routine.
Users new to WatchGuard will find initial configuration confusing as it uses application proxies for the various security services. However, you have an excellent selection of proxies including ones for HTTP, FTP, SIP, H.323, POP3 plus SMTP. Even HTTPS is included as standard.
Proxies are configured and then applied to selected network interfaces using firewall rules. To use the WebBlocker hosted filtering service, for example, requires a profile created which defines which of the 56 URL categories you want blocked.
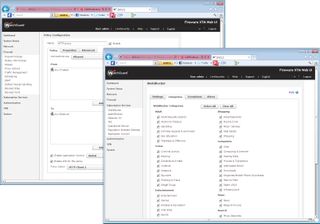
Proxies are used extensively to control traffic and include the WebBlocker URL filtering service
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.

