Gateway AV and anti-spam
Gateway AV provides a global policy that you can assign to any port zone. Scanning for HTTP, SMTP, POP, IMAP and CIFS can be enabled individually and for all protocols you can block password protected archives and packaged executables.
The appliance comes with basic anti-spam as you can use RBLs but we've never found these to be very useful. You're better off paying for SonicWALL's anti-spam service as it's far more effective.
This uses a scoring system to classify messages as definite or probable spam, phishing or infected and you can reject, delete or tag them. The Junk Store feature will prove useful as you can install it on your Exchange Server and allow users to inspect their personal quarantine areas and delete or release messages.
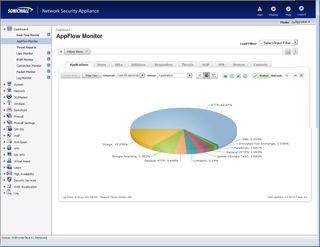
The AppFlow Monitor keeps track of all web apps and you can use this screen to create new application rules on the fly
Application Controls
The Application Control option is designed to provide more versatile policing of web browsing activities, file transfers, email and email attachments. It can provide data leakage protection by scanning emails and files, checking message content, subjects, senders and recipients and blocking file types.
You can use it to control FTP transfers or HTTP requests and apply actions such as blocking or redirecting and limiting bandwidth for certain types of file transfers. It can also handle VoIP services as it can identify and prioritise SIP and H.323 traffic.
A useful feature is the ability to view the AppFlow Monitor from the web console's dashboard and see all application related activity. If you see an app pop up that you don't like the look of you can quickly create a rule that either blocks it, applies a bandwidth management policy or monitors its traffic.
You can go deeper with advanced application rules as these use signature IDs to identity specific activities. The appliance can spot actions such as Facebook pokes, Hotmail attachments uploads, Skype logins the list is endless and either block or log this activity.
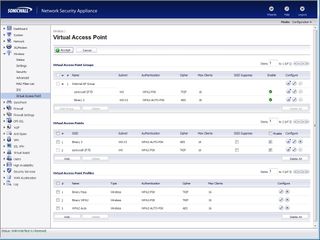
They're tricky to set up but the virtual wireless APs can present a range of guest services each with their own set of security policies
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.

