Wi-Fi hijacker Trojan masquerades as Android apps
Switcher Trojan can hack your router's DNS requests

A Trojan posing as a number of Android apps has been discovered in the wild, capable of hacking Wi-Fi routers and hijacking DNS requests, according to security firm Kaspersky.
Disguised as legitimate Android apps, the Switcher Trojan is able to trick users into submitting personal details by displaying fake webpages masquerading as regular sites.
This new technique involves intercepting daily internet navigation requests by targeting vulnerable Wi-Fi routers, instead of hacking a device directly.
Once a malicious app is downloaded to a device, the Trojan can redirect users to malicious websites by intervening in the process of typing a website's domain name, and the domain name server returning the actual address.
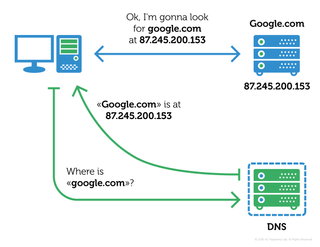
Kaspersky explains: "When you enter google.com, the respective DNS server returns the IP address 87.245.200.153 that is where you are effectively being directed. The thing is, malefactors can create their own DNS server that returns another IP address (say, 6.6.6.6) in response to your "google.com" request, and that address might host a malicious website. This method is called DNS hijacking."
Here's how a normal DNS request would work:
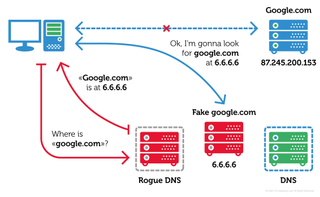
And this is what a DNS request looks like after a Switcher hijack:
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
So how does it get onto your device in the first place? Switcher's developers created a couple of Android apps, one of which imitates Chinese web search app Baidu, while another pretends to be a public Wi-Fi password search app; both are popular in China.
Anybody downloading these apps installs the Switcher Trojan, which then confirms its installation to a command and control server, before brute forcing the victim's Wi-Fi router.
Gaining access to a router allows the Trojan to change the default DNS settings to a malicious address, meaning users searching for Google will instead be directed to a rogue site.
As a final flourish, a legitimate secondary default DNS address is set so that if the rogue server goes down, users will have no idea that any settings were changed.
Kaspersky security experts were able to access Switcher Trojan statistics, which were accidently left open on a public section of the server website. If correct, the Trojan has infected 1,280 networks in less than four months, granting snoopers access to all user traffic and any details entered into malicious websites.
The security firm recommends that, as always, changing the default settings of routers is the most reliable way of preventing these kinds of attacks. Default credentials supplied with every network router are often left unchanged by the user, something that has been exploited by hackers creating IoT botnets for massive DDoS attacks in 2016.
Kaspersky has also warned users to stay clear of suspicious apps on mobile devices and install reputable antivirus software for added protection.
Pictures courtesy of Kaspersky Lab
Dale Walker is the Managing Editor of ITPro, and its sibling sites CloudPro and ChannelPro. Dale has a keen interest in IT regulations, data protection, and cyber security. He spent a number of years reporting for ITPro from numerous domestic and international events, including IBM, Red Hat, Google, and has been a regular reporter for Microsoft's various yearly showcases, including Ignite.





