
Rene Millman
Rene Millman is a freelance writer and broadcaster who covers cybersecurity, AI, IoT, and the cloud. He also works as a contributing analyst at GigaOm and has previously worked as an analyst for Gartner covering the infrastructure market. He has made numerous television appearances to give his views and expertise on technology trends and companies that affect and shape our lives. You can follow Rene Millman on Twitter.
Latest articles by Rene Millman

11 of the best machine learning courses for 2024
By Rene Millman last updated
In-depth The best machine learning courses for helping to kickstart your career in an industry at the cutting-edge of technological innovation

Machine learning vs deep learning vs neural networks: What’s the difference?
By Rene Millman last updated
In-depth These three subdivisions of AI pose different opportunities for businesses

Understanding ransomware attacks and how to ensure your business has a safeguarding strategy fit for today and tomorrow
By Rene Millman published
Sponsored Digital threats loom larger than ever, ransomware stands out as a formidable challenge for organizations worldwide

What is a 502 Bad Gateway error?
By Rene Millman last updated
In-depth We explain what the 502 Bad Gateway networking error means for users and website owners, and some potential steps for fixing it

The UK's best free coding courses
By Rene Millman last updated
Best A list of some of the best free coding courses in the UK to kickstart your career in software development and programming

The best secure smartphones
By Rene Millman last updated
Best Finding the most secure phone for your business helps keep your data and privacy protected
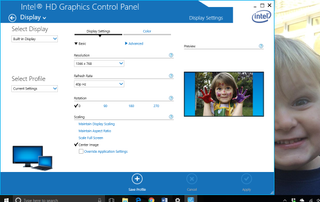
How to rotate a laptop or PC screen
By Rene Millman last updated
In-depth A guide on how to rotate a laptop or PC screen to a different orientation on Windows 10 and 11

What is HTTP Error 503 and how do you fix it?
By Rene Millman last updated
In-depth The cause of HTTP Error 503 might be hard to find, but there are steps you can take to resume website access

How to use a Chromecast without Wi-Fi
By Rene Millman last updated
Tutorials Google’s streaming stick is a great travelling companion, and it's possible to make full use of a Chromecast without Wi-Fi access

How cloud-native agility helped DNEG level up its award-winning VFX
By Rene Millman published
Case study Through Red Hat OpenShift’s cloud-native approach, renowned VFX innovator DNEG slashed its update times

How digital experience management helped an NHS trust improve productivity
By Rene Millman published
Case study Princess Alexandra Hospital NHS Trust used digital experience management to cut device failure and restore time to clinicians

Data science vs data analytics: Which field is right for you?
By Drew Turney last updated
In-depth A career as a data analyst or a data scientist can be as rewarding as it is lucrative, but it pays to understand the subtle differences between the two

Everything you need to know about Citrix
By Keumars Afifi-Sabet, Rene Millman last updated
In-depth We explore the 30-year history of Citrix, its transition from on-premises virtualization to cloud services, key acquisitions, and its focus on secure digital workspaces and workloads

Everything you need to know about HPE
By Jane McCallion last updated
In-depth We recap the 80+ year history of enterprise tech giant HPE, its split from HP, expansive product portfolio, and key acquisitions

Why Vistaprint migrated from on-prem to SAP S/4HANA
By Rene Millman published
Case Study Vistaprint, a provider of marketing products for more than 20 years, decided to migrate to transform its business operations

How to truly unlock seamless collaboration across your business
By Rene Millman published
Sponsored Fragmented data storage can inhibit team productivity. By converging private and public cloud capabilities, a hybrid solution offers unified access and simple workstream coordination…

What is server redundancy?
By Rene Millman last updated
In-depth Server redundancy helps IT administrators get reliable performance from a complex system when a million things can go wrong.

How Photobox unified observability to slash incident response times
By Rene Millman published
Case Study How Photobox gained end-to-end visibility and slashed incident response times across its hybrid landscape

The best C++ courses to kickstart your software development career
By Keri Allan last updated
In-depth Some of the best C++ courses available today for landing a new job, from entry level courses to full certificates

How to speed up Windows 10
By Rene Millman, Jane McCallion last updated
Tutorials Learn which Windows 10 services to disable to boost performance, plus other top tips

How Lush aligned its disjointed customer support operations
By Rene Millman published
Case Study When boutique beauty brand Lush sought to merge its separate US and global customer care operations, it turned to Zendesk
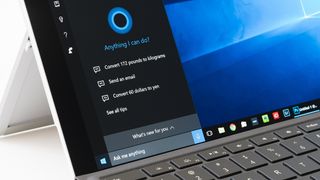
How to factory reset Windows 10
By Rene Millman last updated
Tutorials If your Windows 10 system isn't playing ball, you can reset it back to its factory conditions

The best Google Analytics courses and certificates for 2024
By Rene Millman last updated
In-depth Boost your marketing and audience development skills with some of the best Google Analytics courses and certificate programs around


