McAfee’s MVISION XDR takes security beyond the endpoint
Cloud-native MVISION XDR tool detects threats and predicts countermeasures before a system is compromised
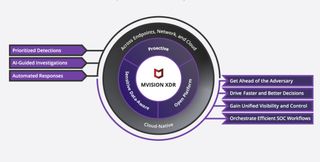
McAfee has announced its new proactive threat detection and response tool for enterprises, MVISION extended detection and response (XDR).
Designed for endpoint, cloud, and network security management, MVISION XDR allows for faster security investigations, easier automated responses, and continued modernization of existing security operations centers (SOC).
“Security teams are struggling to replace reactive, manual and time-consuming investigation processes to combat more sophisticated and more frequent attacks – all while trying to decrease the cost and complexity of overall management,” said Shishir Singh, chief product officer at McAfee.
“MVISION XDR provides proactive and actionable context across key vectors to simplify, accelerate and automate threat validation and response across the enterprise thereby making the most of SOC resources and mitigating potential disruption to the business.”
By granting analysts greater control and a more comprehensive view of threat context beyond endpoints, McAfee’s new cloud-native tool offers a better understanding of threats – before organizations incur damage.
Other MVISION XDR benefits include:
- Proactive and actionable intelligence that prioritizes threats and prescribes countermeasures
- Artificial intelligence (AI)-guided investigations to simplify probes across sophisticated threat campaigns
- Cloud threat integration to provide context for web activity
- Network telemetry prioritization to offer a better understanding of network threats by automatically correlating with curated threats
- Efficient integration with existing SOC infrastructure and tools for maximum return on SOC investment

Managing security risk and compliance in a challenging landscape
How key technology partners grow with your organisation
“Organizations can no longer afford ineffective disparate threat and response tools and context,” adds Jon Oltsik, senior principal analyst at Enterprise Strategy Group.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
“With XDR, we are seeing an opportunity to take the SOC as we know it to the next level – moving from operating in a time and resource intense reactive manner with existing, disparate tools to using a comprehensive and integrated XDR solution that can not only proactively predict mal-activity, but also help drive faster remediation decisions with automation.”
Most Popular





