Equifax data breach: Ex-CIO to serve four months in prison for insider trading
Jun Ying “abused the trust placed in him” to profit from advanced knowledge of the disastrous data breach


The former chief information officer (CIO) of embattled firm Equifax has been sentenced to four months in prison and handed a substantial fine for insider trading following the company's data breach disaster.
Jun Ying, 44, was found guilty of selling $950,000 worth of company shares in March after learning that Equifax had sustained a data breach in 2017, according to the US Attorney's Office for the Northern District of Georgia.
This amounted to illicit trading because Ying managed to avoid losses of $117,000 through the sale, before the data breach news became known to investors, or entered the public domain.
Alongside a four-month prison sentence, the ex-CIO was last week ordered to pay restitution amounting to $117,117.61, as well as a $55,000 fine.
"Ying thought of his own financial gain before the millions of people exposed in this data breach even knew they were victims," said US Attorney Byung J Pak.
"He abused the trust placed in him and the senior position he held to profit from inside information."
The former company executive texted a colleague on 25 August that the breach "sounds bad" and that the company itself may have been the victim.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
The following week, Ying made internet searches to learn about the impact of Experian's data breach on the firm's stock price. He then exercised his stock options to receive 6,815 shares of Equifax stock, which he then sold immediately.
Equifax hadn't publicly declared the breach until 7 September in 2017, after which point the firm's stock price fell considerably.
Ying is the second Equifax employee to have been found guilty of insider trading following the data breach. Sudhakar Reddy Bonthu, a former manager at the company, pleaded guilty to insider trading last year.
13/05/19: Incident has cost the firm $1.4 billion so far
The greatest security catastrophe of modern times has cost Equifax more than a billion dollars to date, according to the firm's latest financial results.
The 2017 data breach incident saw the US-based credit rating agency expose more than 145 million people's personal records to hackers due to flaws in its systems. The breach was sizeable, but deemed highly alarming due to the nature of the information stolen; ranging from full names and addresses to credit card information.
Equifax has now revealed that costs relating to the incident, as well as expenditure on IT and data security, have reached $1.35 billion, excluding a raft of legal fees for lawsuits that are yet to be seen.
This stands at more than 350 times the average cost relating to a data breach, according to IBM research released last year, which found that these costs normally average $3.86 million for a large breach. Even for US-based breaches, which cost $7.91 million on average, Equifax's costs are 170 times greater.
For the first quarter of 2019 alone the company incurred $786.8 million dollars in costs, including $690 million in legal expenditure. The total sum also included $82.8 million for technology and data security, $12.5 million for legal and investigative fees, and $1.5 million for product liability.
The company's chief executive Mark Begor told investors in a conference call that Equifax had made progress since the 2017 breach, according to WABE. This is notably by settling legal action brought against the firm.
While costs relating to the Equifax breach are extraordinary by conventional standards, they fall short of the gargantuan $4 billion 'worst-case' figure once tied with the 2011 Epsilon breach.
This sum was determined by research into the incident at the time, which suggested the estimated total damage could hit between $3 to $4 billion over time, when forensic audits, monitoring, litigation and lost business were taken into account.
20/09/18: Equifax hit with maximum 500,000 fine after a massive security breach
The Information Commissioner's Office (ICO) has fined Equifax 500,000 for failing to protect millions of UK citizens' personal data during a cyber attack last year.
Contact information, email addresses and credit card information of 15 million UK Equifax customers were compromised in a massive hack on its US parent company, Equifax Inc, between 13 May and 30 July 2017.
Although systems in the US were targeted, the ICO found the credit agency's UK arm failed to take appropriate steps to ensure its parent firm, which processed this data on its behalf, had protected the information.
"The loss of personal information, particularly where there is the potential for financial fraud, is not only upsetting to customers, it undermines consumer trust in digital commerce," said Information Commissioner Elizabeth Denham.
"This is compounded when the company is a global firm whose business relies on personal data. We are determined to look after UK citizens' information wherever it is held.
"Equifax Ltd has received the highest fine possible under the 1998 legislation because of the number of victims, the type of data at risk and because it has no excuse for failing to adhere to its own policies and controls as well as the law."
The hack led to the theft of 146 million customers' data from around the world. Although the vast majority of the 15 million UK users affected only had their contact information stolen, it is thought 30,000 also lost their email addresses, and a further 15,000 had partial credit card information stolen.
Equifax received the ICO's Monetary Penalty Notice on Wednesday, and are considering the points made in the document, a spokesperson confirmed. It also once again apologised for the incident.
"Equifax has cooperated fully with the ICO throughout its investigation, and we are disappointed in the findings and the penalty," a spokesperson from its UK arm said.
"As the ICO makes clear in its report, Equifax has successfully implemented a broad range of measures to prevent the recurrence of such criminal incidents and it acknowledges the strengthened procedures which are now in effect.
"Data security and combatting criminal digital activity is an ongoing battle for all organisations that requires continued innovation and attention. We have acted and continue to act to make things right for consumers. They will always be our priority."
The 500,000 fine is the culmination of up to a year's long investigation the ICO has been conducting in tandem with the Financial Conduct Authority (FCA).
It has been adjudicated under the Data Protection Act 1998 (DPA), as opposed to the EU's General Data Protection Regulation (GDPR), since the cyber attack occurred before the new laws came into force on 25 May.
The joint probe revealed multiple failures at the credit agency, including that data was retained longer than necessary, and that personal information was vulnerable to unauthorized access.
Investigators also found significant problems with data retention, IT system patching, and its auditing procedures. The US Department of Homeland Security, moreover, had warned its parent firm about a critical vulnerability as far back as March 2017. Steps to address this vulnerability were not taken, and a user-facing portal was not appropriately patched.
"Many of the people affected would not have been aware the company held their data; learning about the cyber attack would have been unexpected and is likely to have caused particular distress," Ms Denham added.
"Multinational data companies like Equifax must understand what personal data they hold and take robust steps to protect it. Their boards need to ensure that internal controls and systems work effectively to meet legal requirements and customers' expectations.
Denham added that Equifax showed "serious disregard" for their customers and the personal information that it held.
This massive penalty follows the ICO's intent to fine Facebook 500,000 in light of the Cambridge Analytica scandal, with notice issued in July.
However, an ICO spokesperson confirmed the regulator has yet to issue the fine itself, having until January to do so. This means Equifax Ltd becomes the first company to be fined the maximum permitted under the DPA.
Telecoms firm TalkTalk was fined 400,000 in 2016 for a data breach involving over 150,000 customers, and then 100,000 after the discovery of a second hack that occurred earlier in 2014, and therefore collectively has faced similar financial penalties.
Although GDPR has been in force for nearly four months, the ICO has yet to conclude any of its ongoing investigations into breaches of the new legislation.
This includes the breach on Ticketmaster's systems in late June, which could be a litmus test for how the ICO will regulate organisations under GDPR. British Airways could potentially face a 500 million fine, though this would be the maximum.
While the maximum fine under the DPA 1998 is 500,000, breaches of GDPR could see organisations hit with a penalty of up to 17 million, or 4% of an organisation's annual turnover, whichever is higher.
13/02/18: Equifax admits even more data stolen than previously thought
Equifax has admitted that the hack on its systems in late 2017 was far worse than previously thought and that criminals were able to steal sensitive personal information on 145 million customers in the US, UK and Canada.
The international credit agency previously said that hackers were able to access names, addresses, dates of birth and credit score data from user accounts during the breach, as well as financial information and driver licences in some instances.
Although the vast majority of the 15 million UK users affected had only their contact information stolen, it was thought that 30,000 also had their email addresses leaked, and around 15,000 had partial credit card information stolen.
However, it's now emerged that hackers were also able to access US taxpayer ID numbers and their associated email addresses and phone numbers, according to documents disclosed by Equifax to the US Senate Banking committee, seen by the Associated Press.
The documents, provided by Senator Elizabeth Warren's office, also revealed that finer details, such as credit card expiry dates and issuing states for driving licences associated with the taxpayer records had also been leaked.
Equifax spokeswoman Meredith Griffanti said that "in no way did we intend to mislead consumers", and that the company wished only to "act with the greatest clarity" when it decided to disclose only those details relating to the greatest number of users.
She added that the document provided detailed every potential data type that may have been accessed by criminals, but that as a whole they affected a relatively small proportion of users.
"When you are making that kind of announcement, where do you draw the line? If you saw the list we provided the banking finance committee it was pretty exhaustive," said Griffanti, speaking to the Associated Press. "We wanted to show them that no stone was left unturned."
However, this will likely be seen as yet another example of the company trying to mitigate the fallout from a catastrophic data breach. Equifax was first criticised for waiting months before disclosing the hack to the public, and then again when it repeatedly revised up the number of those affected and the types of data potentially lost.
In October the UK Treasury Committee called the company to answer questions relating to its failure to patch a well known Apache Struts flaw, which was thought to have created a hole in its security systems. This was shortly followed by the news that the Financial Conduct Authority would be investigating the hack, including Equifax's subsequent handling of it.
Outside of regulatory investigations, the company also faces hundreds of lawsuits brought by customers, and is thought to have set aside almost $90 million to deal with the fallout.
13/11/2017: Hack costs Equifax $87.5 million, as income plummets
Equifax's data breach has cost the company $87.5 million, its latest financial results reveal.
The credit monitoring agency's failure to patch a server flaw over summer resulted in hackers potentially stealing 143 million US citizens' data, and that of 700,000 Brits.
It's set aside $87.5 million ($59.3 million net of tax) to deal with the fallout from the hack, recording the expense in its July-September financial quarter.
Releasing its results for the quarter last week, Equifax revealed that its operating income fell by 28% year-on-year to $152.9 million as a result of the financial hit.
However, it could get even worse, with the firm admitting the total cost of the hack could hit $110 million.
Of the money it's set aside, $55.5 million accounts for the cost of providing hack victims with a free credit file monitoring and identity theft protection service, with a further $17.1 million spent on professional services. Customer support is costing Equifax $14.9 million.
The results update read: "We have incurred $4.7 million through September 30, 2017 [due to the breach] and have estimated a range of additional costs between $56 million and $110 million.
"We have recorded a liability for the low end in the range as we do not believe that any amount within the range is a better estimate than any other amount."
Hack victims who haven't signed up for Equifax's free credit file monitoring and identity theft protection service have until 31 January 2018 to do so.
26/10/2017: Credit agency says victims can still sue, despite rule change
Equifax has denied customers affected by the hack that saw the personal details of millions taken by cyber criminals will be unable to sue the company.
It had been speculated that those affected would be prevented from suing the company, after the US Senate yesterday repealed a law that prohibited "covered providers of certain consumer financial products and services from using an agreement with a consumer that provides for arbitration of any future dispute between the parties to bar the consumer from filing or participating in a class action concerning the covered consumer financial product or service".
Equifax, however, is standing by earlier statements that customers will be able to file a lawsuit if they wish.
In a statement, the company told IT Pro: "Enrolling in the free credit file monitoring and identity theft protection products that we are offering as part of this cyber security incident does not prohibit customers from taking legal action. The congressional action overturning the CFPB's rule does not change our position."
The mention of the free credit file monitoring and identity theft protection products is significant in itself. When these initiatives were first launched, there was a clause in the terms of use that it appeared would have prevented customers for suing the company for the breach. Following public outcry, however, the company clarified that the stipulation referred only to these products, not to the breach itself.
Over 140 million consumers globally were affected by the hack, which took place between May and July 2017, but wasn't discovered until 29 July. No public announcement was made until mid-September.
25/10/2017: Hack victims may not be able to sue Equifax
The US Senate voted early this morning to remove a federal rule that would have allowed people affected by the Equifax hack to sue the company.
A 50/50 tie-break in the Senate was broken by vice-president Mike Pence casting a deciding vote in favour of the joint resolution to get rid of the rule, TechCrunch reported.
The rule in question stops financial services companies that bind their users by arbitration agreements from preventing them from suing as a class.
It was entered into the Federal Register in July by the Bureau of Consumer Financial Protection, with the joint resolution to nullify it - H.J Res.111 - submitted the next day.
The rule says: "The final rule prohibits covered providers of certain consumer financial products and services from using an agreement with a consumer that provides for arbitration of any future dispute between the parties to bar the consumer from filing or participating in a class action concerning the covered consumer financial product or service."
Equifax pointed customers affected by its huge data breach to sign up to its TrustedID Premier service in the aftermath of the hack. TrustedID offers identify theft insurance and scans the web to see if customers' social security numbers have been used illegally.
Initially, the terms of service of TrustedID made clear that signing up to use it prevented users from suing the company and ensured any disputes it had would need to be resolved through arbitration.
Equifax then removed the arbitration clause last month, and said in an FAQ that neither the TrustedID terms of use nor Equifax's own terms of use would prevent people from taking legal action.
It still reads: ''We will not apply any arbitration clause or class action waiver against consumers for claims related to the free products offered in response to the cybersecurity incident or for claims related to the cybersecurity incident itself''.
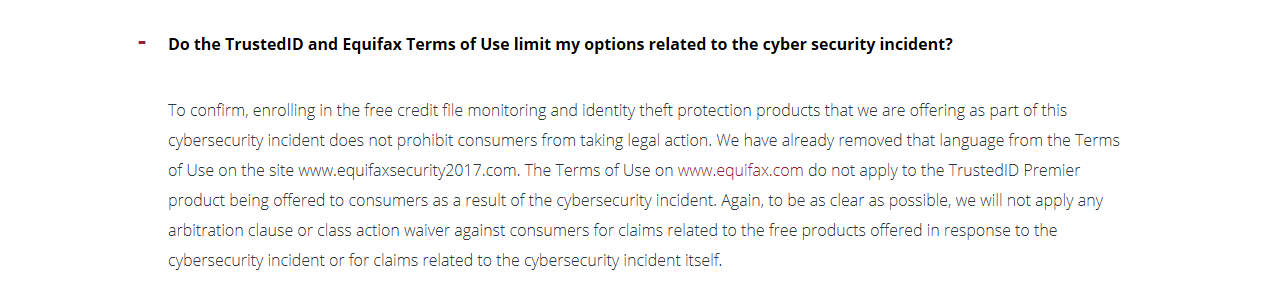
From Equifax's TrustedID Premier FAQ
Despite this, it remains unclear what users have signed up for and whether the striking of this federal rule will affect them.
IT Pro has asked Equifax whether people will still be able to use TrustedID Premier, and Equifax's credit monitoring services, and be able to sue it over its cyber security breach, if the rule is nullified.
All that is needed for the rule to be thrown out is for the joint resolution to be signed by president Donald Trump.
24/10/2017: FCA opens investigation into Equifax hack
The Financial Conduct Authority (FCA) has confirmed it's investigating the Equifax hack in which the details of 700,000 Brits were leaked.
The financial watchdog said it was confirming the investigation "given the public interest in these matters."
"The FCA announces today that it is investigating the circumstances surrounding a cybersecurity incident that led to the loss of UK customer data held by Equifax Ltd on the servers of its US parent," the watchdog said, giving no other detail on the inquiry.
In a statement, Equifax said it looked forward to the results of the investigation. "We welcome this opportunity to learn the lessons from this criminal cyber attack in order for all businesses to better protect consumers in the future," it said. "Cybercrime is a real and ever-present risk faced by all companies, so it is important that government, regulators and businesses work together to combat this growing threat. We see today's announcement as a continuation of that process."
As many as 143 million Americans were affected by the data breach, alongside 700,000 in the UK, but Equifax took months to notify victims. Leaked details included phone numbers, driving licence numbers, usernames and passwords, and emails.
13/10/2017: UK Treasury Committee chair demands answers from Equifax over data leak
Equifax could potentially face political backlash over its handling of its recent data leak, as the chairman of the House of Commons has now demanded answers as to why it took so long for UK customers to be alerted.
The head of the treasury select committee, Nicky Morgan, has written a letter to the credit agency's European chief Patricio Remon asking for the full scope of the data breach, and what compensation will be provided to those affected. A letter has also been sent to the Financial Conduct Authority (FCA) to see whether the watchdog plans to move against the UK arm of Equifax.
The company revealed on 7 September that a data breach on its systems in mid-May had resulted in the leak of 143 million data records, later revised up to 145 million. The hack, which was thought to have affected mainly the US systems, was blamed on the company failing to apply an Apache Struts patch, which was known to have been vulnerable.
The company also initially said that 400,000 UK customers had been indirectly affected by the breach, but that no financial details had been accessed.
However, on Tuesday Equifax made yet another revision, admitting that a file containing data on 15.2 million UK records was accessed during a data breach in May, giving access to names and contact details, and of that figure almost 700,000 accounts had had partial credit information and email addresses stolen.
"Equifax has taken too long to notify those affected by its widespread cyber-security breach," said Morgan. "People have been left in the dark for too long, which has increased the risk that they fall victim to identity theft and fraud."
She added that the Treasury Committee will "consider taking public evidence from Equifax, particularly if it does not receive a full and timely response to these questions".
Equifax is facing mounting pressure from both customers and lawmakers to explain why customers are only hearing about the data leak now, and why the company continues to botch its handling of the situation weeks after going public.
Part of the investigations will look into Equifax's handling of its customer help website, which was forced offline this week over concerns it contained malware. An independent security analyst discovered that customers were being asked to download outdated versions of flash player, according to Ars Technica, although Equifax said its systems "were not compromised and that the reported issue did not affect our customer online dispute portal".
The company also used the website 'equifaxsecurity2017.com' as its official breach handling portal, which understandably drew complaints that it looked like a phishing site, and customers complained that its site designed to inform users if their data had been leaked was returning false results.
Political movements in the US are seeking to clamp down on credit agencies in the wake of the industry's largest ever data breach. Democratic senator Elizabeth Warren said last week that "Equifax and this whole industry, should be completely transformed", the Financial Times reports, and that the Equifax data breach, which affected almost half of the American adult population, is evidence of a disregard for the security of customers.
It's likely that Equifax will be asked to appear before a UK committee, although there are no specific demands in place. Equifax's US boss Rick Smith, who stepped down in the wake of the data breach, was asked explain himself in front of a US house committee last week.
11/10/2017: Nearly 700,000 Brits affected by Equifax breach
Nearly 700,000 UK citizens were badly affected by Equifax's data breach, the credit monitoring agency admitted yesterday, revising its initial figure of 400,000.
A huge data set of 15 million UK credentials was also attacked during the raid between May and July, though once Equifax analysed the data it found only 694,000 UK customers who it needed to contact - many of the remaining records consisted of spurious fields and duplicated entries, though others contained names and dates of birth.
"Whilst this does not introduce any significant risk to these people Equifax is sorry that this data may have been accessed," the company said in a statement.
The 694,000 Equifax is now writing to had various data leaked - the vast majority had their phone numbers leaked, 30,000 had their email addresses breached, and 15,000 had their login details and partial credit card details from 2014 leaked, despite earlier statements saying that UK financial data had not been accessed.
Equifax alerted the UK's National Cyber Security Centre, which has put out an advisory statement to affected customers.
"Equifax has today confirmed that a file containing 15.2m UK records dating from between 2011 and 2016 was attacked in the cyber incident that took place in May 2017," A NCSC statement said on Tuesday.
"If you have been told by Equifax that security details from your Equifax.co.uk membership account - such as password and secret questions - have been accessed, you should ensure those details are not used on any other accounts."
Equifax reported in September that it had been the victim of a major data breach between May and July this year, in which 143 million US customers were thought to have been affected, and an undisclosed number of UK and Canadian customers. That figure has since risen to 145.5 million, and recent reports have suggested that as many as 11 million US driver's licenses were leaked during the raid.
It was later found that hackers were able to exploit a months-old flaw in the application framework Apache Struts, which had a patch available, though Equifax failed to apply it. Social security numbers, dates of birth, addresses, credit card details and security information were all thought to have been compromised during the breach.
The NCSC believes the greatest risk will come from subsequent phishing campaigns using leaked personal data. Customers have been warned that given the nature of the data leak, fraudsters will likely use real names in the emails to make the phishing attacks look more genuine.
"The NCSC, with Equifax and partners including the NCA, ICO and FCA, continues to examine this incident and should further information come to light about the extent and nature of the impact on the UK, we will provide further updates and advice as soon as we can," a spokesperson said.
Patricio Remon, president for Europe at Equifax's UK unit, said: "Once again, I would like to extend my most sincere apologies to anyone who has been concerned about or impacted by this criminal act. Let me take this opportunity to emphasise that protecting the data of our consumers and clients is always our top priority."
"It has been regrettable that we have not been able to contact consumers who may have been impacted until now, but it would not have been appropriate for us to do so until the full facts of this complex attack were known, and the full forensics investigation was completed."
Main image credit: Bigstock

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.
-
 CISO warns agentic AI tied to major risks and failure
CISO warns agentic AI tied to major risks and failureNews Runtime security and employee oversight are necessary to achieve success with AI agents, according to Haider Pasha
-
 Enterprise browsers: the new standard for security?
Enterprise browsers: the new standard for security?In-depth The market for enterprise browsers is growing fast – but are their features and security controls enough to compete with free applications?
-
 Scania admits leak of data after extortion attempt
Scania admits leak of data after extortion attemptNews Hacker stole 34,000 files from a third-party managed website, trucking company says
-
 Capita tells pension provider to 'assume' nearly 500,000 customers' data stolen
Capita tells pension provider to 'assume' nearly 500,000 customers' data stolenCapita told the pension provider to “work on the assumption” that data had been stolen
-
 Gumtree site code made personal data of users and sellers publicly accessible
Gumtree site code made personal data of users and sellers publicly accessibleNews Anyone could scan the website's HTML code to reveal personal information belonging to users of the popular second-hand classified adverts website
-
 Pizza chain exposed 100,000 employees' Social Security numbers
Pizza chain exposed 100,000 employees' Social Security numbersNews Former and current staff at California Pizza Kitchen potentially burned by hackers
-
 83% of critical infrastructure companies have experienced breaches in the last three years
83% of critical infrastructure companies have experienced breaches in the last three yearsNews Survey finds security practices are weak if not non-existent in critical firms
-
 Identity Automation launches credential breach monitoring service
Identity Automation launches credential breach monitoring serviceNews New monitoring solution adds to the firm’s flagship RapidIdentity platform
-
 Neiman Marcus data breach hits 4.6 million customers
Neiman Marcus data breach hits 4.6 million customersNews The breach took place last year, but details have only now come to light
-
 Indiana notifies 750,000 after COVID-19 tracing data accessed
Indiana notifies 750,000 after COVID-19 tracing data accessedNews The state is following up to ensure no information was transferred to bad actors