Endpoint Security
Latest about Endpoint Security

The Total Economic Impact™ of IBM Security MaaS360 with Watson
By ITPro published
Whitepaper Cost savings and business benefits enabled by MaaS360

Unified endpoint management and security in a work-from-anywhere world
By ITPro last updated
Whitepaper Learn how to converge endpoint management and security processes and systems to drive efficiency and reduce risk
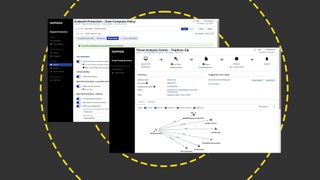
Sophos Intercept X Advanced review: A huge range of endpoint protection measures for the price
By Dave Mitchell last updated
Reviews A superb range of security measures and a well-designed cloud portal make endpoint protection a breeze
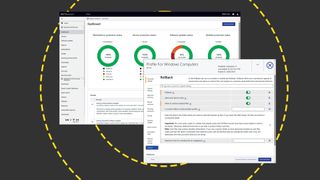
WithSecure Elements EPP and EDR review: Endpoint protection on a plate
By Dave Mitchell published
Reviews An affordable cloud-managed solution with smart automated remediation services
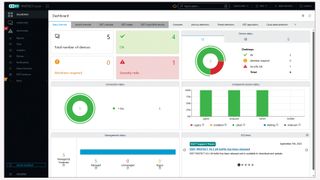
Eset Protect Cloud Advanced review: An impressive arsenal of endpoint protection features
By Dave Mitchell published
Reviews Policy management is complex, but Eset offers an affordable and flexible cloud-hosted solution

KuppingerCole leadership compass report - Unified endpoint management (UEM) 2023
By ITPro published
Whitepaper Get an updated overview of vendors and their product offerings in the UEM market.

The Total Economic Impact™ of IBM Security MaaS360 with Watson
By ITPro published
Whitepaper Get a framework to evaluate the potential financial impact of the MaaS360 on your organization

Unified endpoint management software vendor assessment
By ITPro published
Whitepaper Make positive steps on your intelligent automation journey
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.





