IT Pro Verdict
We were impressed with the Performa’s easy deployment and excellent anti-spam performance in our live tests. It offers plenty of other security features and the web interface is very intuitive but the Cobion URL web filtering category database could do better.
It may be best known for its anti-virus software products but Panda moved into the security appliance market a number of years ago and now offers an extensive range of hardware solutions. The GateDefender Performa family focuses on delivering web content security at the network perimeter and the latest 9100 now adds controls for IM and P2P apps to its anti-spam, anti-malware and web content filtering features.
As the 9100 functions as a transparent gateway it's a cinch to deploy. We popped it in between our LAN and firewall enabling it to scan inbound and outbound HTTP, FTP, SMTP, POP3 and NNTP protocols without any need to reconfigure our network clients.
The appliance comes as standard with a dual-port Gigabit card which has a hardware bypass circuit, so if the system goes belly-up it won't take all internet access with it. For greater fault tolerance it also supports load balancing across a pair of appliances.
The 9100 is the second in a family of four Performa appliances and is designed to handle up to 500Mbps of web traffic and 220 messages per second. The hardware platform looks up to the job as Panda has opted to use a decent Sun Fire X2100 1U rack server equipped with a 2.8GHz dual-core Opteron and 4GB of DDR2 memory.
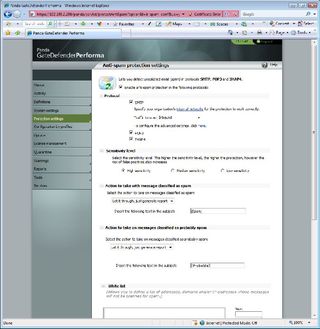
The anti-spam module provides a good range of options for handling suspect emails.
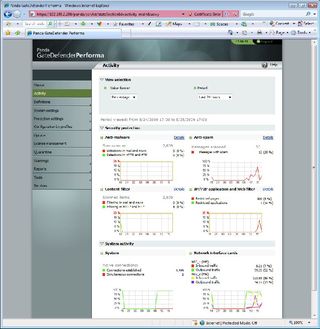
The management web interface is a smart affair that provides easy access to all the features. You have two layers of security as the appliance enforces policy based security settings first followed by global settings for each security module.
To use policies you start by creating network definitions, which describe IP addresses, ranges or subnets, LDAP servers, users and domains. You then access the settings management page where you define custom configurations for the anti-malware, web content filter, URL filter and anti-spam modules.
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.

