Facebook bug catcher reveals hacker value of Zuckerberg wall post stunt
Updated: IT security community rallies to raise funds for unemployed Facebook security bug catcher.
The Palestinian information system specialist that publicly exposed a Facebook security flaw claims he could have made thousands of dollars by selling on information about it to hackers.
Khalil Shreateh, found a vulnerability that allows people to post to anyone else's timeline, irrespective of whether or not the poster and the recipient are friends.
He flagged the issue via Facebook's White Hat security programme, which promises $500 for each flaw found, but the social networking giant denied it was a genuine flaw.
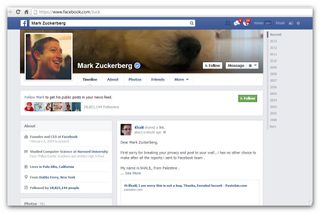
Shreateh responded by stating, "Ok, that mean (sic) I have no choice other than to report this to mark (sic) himself on facebook" and then proceeded to write a post on Facebook founder Mark Zuckerberg's wall about it.
The post from Shreateh to Zuckerberg's Facebook timeline apologised for breaking the billionaire's privacy but said he had "no other choice ... after all the reports I sent to [the] Facebook team".
The message concluded: "I appreciate your time reading this and getting someone from your company team to contact me."
Shreateh claims his account was disabled within minutes of the post with the company initially telling him it had the right to disable any Facebook account without giving a reason.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
Shortly afterwards, a member of the Facebook team said they had disabled his account as a precaution, and that his original submission to the White Hat security team contained insufficient technical information for it to act.
"We cannot respond to reports which do not contain enough detail to allow us to reproduce an issue. When you submit reports in the future, we ask you to please include enough detail to repeat your actions," Facebook is reported to have told him.
"We are unfortunately not able to pay you for this vulnerability because your actions violated our Terms of Service. We do hope, however, that you continue to work with us to find vulnerabilities in the site," it added.
Facebook has confirmed Shreateh's account of events and that the messages he received from the security team are genuine.
Shreateh has since spoken to CNN stating that he could have sold the exploit to blackhat hackers for thousands of dollars, but didn't because he was a "good guy".
"I could sell (information about the flaw) on the black (hat) hackers' websites and I could make more money than Facebook could pay me," he told CNN.
"I never asked [Facebook], 'I want $4,000 or $5,000'," said Shreateh, who has reportedly been unemployed for two years.
"I didn't deal with them like that ... . (But) I really needed that money."
Following the interview, Marc Maiffret, chief technology officer of cybersecurity firm BeyondTrust, set up a fundraising initiative for the Shreateh on GoFundMe to raise awareness of the plight of independent security researchers.
Maiffret set a goal of $10,000 (6,386) in donations and managed to raise $10,830 (6,916) within one day.
On the fundraising page, Maiffret said: "gofundme to transfer the funds to Khalil, whom I am now in contact with. I hope this has raised awareness of the importance of independent researchers.
"I equally hope it has reminded other researchers that while working with technology companies can sometimes be frustrating, we can never forget the greater goal; to help the internet community at large, just as that community has helped donate over ten thousand dollars to Khalil within a day."
- This article was originally published on 19 August 2013 and updated on 21 August to include information on Shreateh's interview with CNN and Maiffret's fundraising effort.

Jane McCallion is ITPro's deputy editor, specializing in cloud computing, cyber security, data centers and enterprise IT infrastructure. Before becoming Deputy Editor, she held the role of Features Editor, managing a pool of freelance and internal writers, while continuing to specialise in enterprise IT infrastructure, and business strategy.
Prior to joining ITPro, Jane was a freelance business journalist writing as both Jane McCallion and Jane Bordenave for titles such as European CEO, World Finance, and Business Excellence Magazine.




