Windows Troubleshooting Platform 'is serving malware'
Troubleshooting service used as a pathway to con victims into downloading malware

Hackers are abusing Windows Troubleshooting Platform (WTP) to trick users into downloading malware onto their computers.
WTP is a legitimate feature in Windows, intended for troubleshooting problems. However, researchers at Proofpoint have found a social engineering attack that uses this normally helpful service as a vector for infection.
In a blog post, the researchers said: "This attack is particularly effective since execution of WTP is not accompanied by a security warning and users have been conditioned to run the troubleshooter when it appears in Windows. In this case, though, running the troubleshooter leads to the installation of LatentBot, a well-documented modular bot used for surveillance, information stealing, and remote access."
The scam runs like this: The target victim receives an email with a file attachment that, when downloaded and opened, looks as if there is an issue with the computer's font set. The user is prompted to "double-click to auto detect charset", which, if followed, opens a real embedded, digitally signed DIAGCAB file - the extension for a Troubleshooting pack.
Once opened, this displays what Proofpoint calls a "convincingly realistic" download wizard (see below). If the user clicks "next" in this window, the malware payload is then downloaded and executed on the computer.
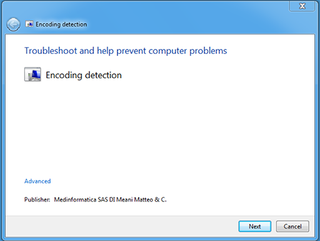
"This method of malware execution bypasses observation by many existing sandbox products because the malicious activity is carried out outside of the msdt.exe binary loading the .diagcab file," said Proofpoint.
"This continues the trend of malware authors seeking new sandbox evasion methods via COM-based non-standard execution flow; previous examples of these methods are WMI, Office Interoperability, Background Intelligent Transfer Service, and the Task Scheduler."
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
The method could, the researchers said, "fool even experienced users", due to how convincing it is and the fact it evades detection by many sandboxing techniques.
IT Pro has approached Microsoft for comment, but had received none at the time of publication.

Jane McCallion is ITPro's deputy editor, specializing in cloud computing, cyber security, data centers and enterprise IT infrastructure. Before becoming Deputy Editor, she held the role of Features Editor, managing a pool of freelance and internal writers, while continuing to specialise in enterprise IT infrastructure, and business strategy.
Prior to joining ITPro, Jane was a freelance business journalist writing as both Jane McCallion and Jane Bordenave for titles such as European CEO, World Finance, and Business Excellence Magazine.




