
A fresh malware found on theGoogle Play Storedisplays pornographic ads and tries to trick users into installing fake security apps'.
To make matters even worse, the malicious code is said to hide itself inside around 60 game apps, many of which are intended to be used by children, and which have been downloaded between 3 million and 7 million times, the researchers who discovered it said.
Those researchers, fromsecurity firm Check Point Research, said the malware - dubbed AdultSwine' - also induces users to register to premium services at their own expense.
Here's how it works: First, the malicious code contacts its Command and Control (C&C) server to report the successful installation, sends data about the infected device and then receives the configurations, which determine its course of operation.
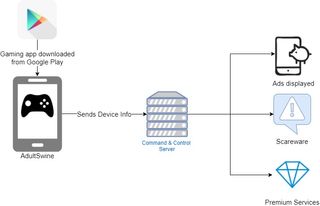
"These configurations instruct it on whether to hide its icon, which ads to display, over which apps and on what terms," Check Point's researchers explained.
"The malicious code then verifies certain conditions regarding the device's status and checks which app is currently running on screen. Once all its terms are met, it begins to display the illegitimate ads outside of the app's context."
If it is embedded inside a web browser app, the ads will be displayed inside that browser, and if not, they will be displayed inside a designated web view, Check Point said.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
"As for the ads being displayed, they come from two main sources; the first is that of the main ad providers, which forbid such illegitimate display of their ads. The second is the malicious code's own ad library, which contains ads of an offensive nature, including pornographic ads."
All of these Check Point highlighted - are displayed to children while playing the game that the app is masquerading as.
"The malicious code can use [also] its infrastructure to broaden its goals to other purposes, such as credential theft," explained Check Point. "Once the malicious app is installed on the device, it waits for a boot to occur or for a user to unlock his screen, upon which it initiates its malicious activity."
"We've removed the apps from Play, disabled the developers' accounts, and will continue to show strong warnings to anyone that has installed them," a Google spokesperson toldReuters.




