Intel Labs: Turning wine into electricity
Chipmaker also cooking up federated security dashboard, and context sensitive smartphones.

Intel fellow, Genevieve Bell showcased a number of research products that Intel is working on during the final day of IDF 2013.
Attendees were treated to demonstrations of ultra-low power boards, clothing prototypes, as well as security and context sensitive software.
Wine into electricity
One of the key messages throughout IDF 2013 has been how hard Intel is focusing on the commercialisation of low-power technology.
"You saw our CEO talk on Tuesday about Quark our most recent generation of low-power mobile technology. But I think we're going to need to go even lower," Bell told attendees.
On stage Intel showed how a glass of wine containing copper and zinc provided enough power to allow a development board to transmit data and manipulate an image on screen.

"Some people turn water into wine. Here at Intel we're turning wine into electricity. Using an experimental low power processor here, what you can see is it's possible to start to imagine a world of incredibly low power, but also really high-performance, which will help do a number of things," Bell continued.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
"One of the things that's compelling to think about low power is that it lets us not only run an object for a really long time, but run an object close to our bodies that has to know something about us."
Federated identity
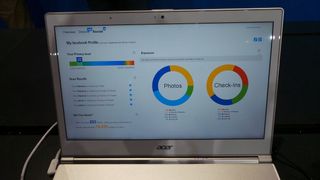
Another interesting demo revolved around an unnamed software dashboard also built in-house at Intel. This allows users to see exactly how much personal information they are sharing with smartphone applications and social networks.
Intel plans to allows users to enrol a variety of devices from Ultrabooks and smartphones to wearables and smartcars, explained Peter Biddle, GM of Intel's cloud services platform.
By registering her smartphone, Bell was able to see that 19 of her apps actually had access to text messages, and 19 could see call history something which she could then be remedied.
Biddle also showed how the software can help people manage social networks such as Facebook. The dashboard may, for example, show a photo that's been marked public, which you didn't know about. You can go directly to the picture in question and change the privacy setting.
Smart clothing
The enhancements in low-power will see an increasing number of smart clothes make it to market. Intel showcased a bike vest prototype from the Fraunhofer Institute in Berlin, giving us an idea of what to expect.

The bike vest uses stretchable and bendable micro-circuitry, which allows it to fit the contours of someone's body.
"Each one of the LED lights has a built in accelerometer and it sparkles for safety. When you look at this what you should think is the future of mobile isn't just devices, some of it is going to be clothing. It's going to be the things that we wear on our bodies," Bell explained.
Contextual smartphone
Bell was also joined on stage by Lama Nachman, a senior staff researcher at Intel, who demonstrated how the chipmaker is working on software to make phones more context sensitive.
"Effectively we have two phones, they know who their owners are because they can hear us, but also know they are together because of proximity. That means you can start to do interesting things in terms of recommendations," Bell said.
Nachman also demonstrated that Intel is working on password-free security features for smartphones using accelerometers.
"My phone can recognise the way I walk because the walking pattern or gait of people is very specific to who they are," said Nachman.
The device unlocked when Nachman walked with it on stage, but when Bell tried to walk off holding it, the handset labelled her as an "imposter" and remained locked.
This type of security isn't quite foolproof. Basing security on walking patterns is tricky as they can change when different footwear is worn but Intel is confident this is something it can overcome.
"Overtime as [the device] learns your [habits] it will know this is what you look like in heels and what you look like on other surfaces," Nachman added.
Unfortunately, everything we saw was in the prototype phase so there are no time frames for commercial release. But based on what we've seen, the security dashboard could be the closest to being ready to commercial deployment.




