IT Pro Verdict
Microsoft Office 365 provides an even more affordable route to the gold standard of office suites, with even more added value from online functionality.
Pros
- +
Use of Microsoft Office desktop apps for a small monthly fee; Powerful desktop software; Capable Web and smartphone versions of main apps; 1TB of storage for every user; Up to five software installations per user
Cons
- -
Live collaboration not as seamless as Google’s G Suite; Enterprise editions required if you need more than 300 users
Once upon a time, there were many different options for office software suites, but these days, most organisations really only select between two alternatives - Microsoft Office 365 and Google's G Suite. Research by Bitglass in 2018 found that the former had a 65% market share, and the latter 19.2%, with the remainder taken up by software such as Apple's Pages and the open-source OpenOffice. Over two articles, we will be looking at what this leading duo of office suites has to offer. Here we delve into Microsoft's Office 365. You can read about G Suite in the accompanying IT Pro review (link).
Microsoft Office 365 review: Options
Although office software used to be primarily about the features of the word processor, spreadsheet, presentation tool and mail client, the suite is now a much more complicated package extending into the cloud. So whilst Microsoft is ostensibly paid-for software and G Suite can be used for free, once you factor in a usable amount of cloud-based services, G Suite also comes with a price tag, and it's broadly equivalent.
There are at least six ways of buying the latest version of Microsoft Office. However, one of these is the traditional "perpetual" method of owning the software outright without regular updates, called Home and Student 2019, which only comes with Word, Excel and PowerPoint and no cloud services. Then there are Home and Personal options for home users. These are subscription services, with Personal charging 59.99 a year for one user, whilst Home is 79.99 for up to six users. Both packages include Word, Excel, PowerPoint and Outlook for PC and Mac, as well as Publisher and Access on PC only. They also include 1TB of OneDrive storage per user and Skype with 60 minutes of calls to mobiles and landlines per month.
For companies, however, there are three main subscription levels - Business, Business Premium, and Business Essentials. The Essentials version is 3.80 per user per month, and doesn't include any desktop software, just services. These comprise Exchange email (accessible via an Outlook Web client), 1TB of OneDrive storage, SharePoint and Microsoft Teams (of which more later). Whilst there's no desktop software included, you can use Word, Excel and PowerPoint via Web-based versions. This is broadly similar to the Basic version of G Suite, in that it's a Web app subscription. It's 50p a month more expensive, but you get a lot more storage for your money (1TB versus 30GB), although you do have to pay an annual fee upfront.
The standard Business subscription costs 7.90 per user per month, whilst Business Premium is 9.40 per user per month, with fees payable annually. Both give you the full set of Office software, including Outlook, Word, Excel, PowerPoint, OneNote and Access, although the latter is PC only. Both give every user 1TB of OneDrive cloud storage, but the Premium version is required if you need Exchange, SharePoint and Microsoft Teams. However, it's worth noting that Microsoft's definition of a user isn't constrained to a single device. Recognising that we now frequently have multiple devices, a user can install software on up to five phones, five tablets, and five PCs or Macs. This goes some way to combatting the "any time on any device" aspect of the cloud-based G Suite.
There are also corporate sub-versions of Office 365, like ProPlus, which is essentially Business with Publisher (PC only) and 24/7 support. Then there are the Enterprise E1, E3 and E5 that add services including Yammer, Stream, and Power BI Pro, which we won't be discussing in detail in this article. One of the key reasons for choosing an Enterprise option over a Business one is that the Enterprise options allow more than 300 users, which the Business options don't. There are no such limits with any version of G Suite.
Microsoft Office 365 review: Applications
Despite the obvious cost incentive of free Web-based office software or open source Open Office, Microsoft's Office applications remain the market leaders and have been regaining ground in the last year or two. All of the subscriptions including desktop software described above also include live updates to the latest versions as they roll out, for the duration of the subscribed period.
At the time of writing, the current Office 365 software included the 2016 application versions, although 2019 will likely become available at some point in the near future. However, it's worth noting that version 2019 is Windows 10 or above only on PC and MacOS 10.12 and above on Apple devices. So businesses that are still maintaining earlier versions of either operating system won't get the latest software from Office 365 even when 2019 does roll out.
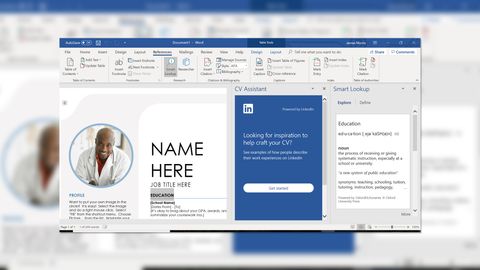
The Office 2016 apps introduced the ability to open and save documents straight from and to OneDrive cloud storage. You can send documents to the desktop versions directly from the Web iterations, and save your edits back to the online repository. This is great for collaboration, although still not as seamless as the G Suite implementation. The interface of Word 2016 hasn't changed much since the 2013 version, although there's now a Share button on the top right that leads you to collaboration capabilities. The default dictionary has been replaced with a Smart Lookup powered by Bing, which provides a richer array of content you can drag into your document, including Wikipedia entries. Another benefit of the new OneDrive connectivity is that if you save your documents to the cloud, it will be kept up-to-date in real time. So you can close your file on the local machine and, for example, open it on your phone to carry on where you left off.
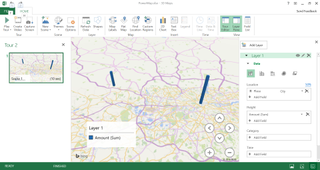
Most of the Excel 2016 updates revolve around the integration of Business Intelligence (BI) features. Excel can Publish workbooks or portions thereof to Power BI, including the ability to export into a Power BI dataset and create reports. A variety of new chart types were introduced with 2016, including waterfall, box & whisker, treemap, sunburst, and histogram - Pareto. These are all popular chart types that are very welcome additions. Another capable new feature is the ability to insert Power Maps, which place data on a 3D map, so you can visualise quantities related to their location. You can automatically create forecasts based on your existing data, and PivotTables now group date fields together for you.
Although Excel doesn't have the native online functionality of Google Sheets, it can import data from a website, as well as a host of different database types. These include SQL Server, MySQL, Access, and IBM DB2 amongst many others. You can also import from Azure cloud storage, and even Facebook, Salesforce repositories and your Exchange email database.
PowerPoint 2016 gets the same cloud collaboration and Smart Lookup abilities as Word and Excel. The preset shape styles now include colour and border options for each shape. You can also change the colour of the UI and save these for your Office 365 account. Most of the same new chart types from Excel are also available in PowerPoint, including treemap, sunburst, histogram, box & whisker and waterfall, which can be directly linked to an Excel spreadsheet. You can now embed online videos into presentations using an embed code, making this more reliable than before.
When the 2016 applications are replaced by 2019 iterations within Office 365, Word 2019 will gain a Focus mode that darkens the rest of the screen and UI around the document you are working on, so you can more easily concentrate. Outlook 2019 will also get a Focused Inbox for streamlining workflow and draft emails. You can read more about the new features here.
Microsoft Office 365 review: Cloud Services and Smartphone Apps
Aside from the switch to a subscription model, Office 365 brought with it a host of cloud services. These include Web-hosted versions of the main productivity software - Word, Excel, PowerPoint and Outlook - so your users can be productive via a browser, even if they don't have access to a system with desktop software installed. In fact, you can use these with a free Microsoft account - you don't need an Office 365 subscription. This comes with the same 15GB of storage as a free Google account.
Outlook on the Web has long provided a desktop-like experience within a browser. In fact, Outlook Web Access first arrived in 1995, and was one of the first systems to use Asynchronous JavaScript and XML (AJAX) to provide responsive apps inside a browser. A new version of Outlook online has recently been released, including more powerful message searching and a scheduling system that tells you when everyone involved in a meeting is free. The Web interface is considerably streamlined compared to the desktop version, lacking for example the powerful rules system. But it's reassuring to see how features like colour-coded categorisation are integrated and mirror from Web to desktop versions.
The Word interface on the Web is relatively fully featured and looks very similar to the desktop version, aside from a handful of differences. The Insert section lacks the ability to create Text Boxes, there's no Design tab, you can't create columns in Page Layout, and you can't create a table of contents in References. The latter also lacks the Research and Citation tools, and there is no Mailings tab. Otherwise, however, this is a very desktop-like experience.
Excel for the Web lacks a bit more, losing the Page Layout and Formulas tabs. However, you can still create PivotTables. The Data section allows you to refresh existing connections to online services, but not create new ones. However, PowerPoint online is virtually identical in design and content features to the desktop version, although curiously the SlideShow presentation options are found in View, which is a bit counterintuitive for seasoned PowerPoint users.
On iOS or Android there are versions of Word, Excel, PowerPoint, OneNote, and Outlook. An Office 365 subscription allows you to install these on five smartphones and five tablets per user. The smartphone apps offer considerably reduced subsets of the Web versions. However, the direct links to cloud-based OneDrive storage mean you can open a document to make some tweaks when on the move, and then do more serious work seamlessly from a browser or desktop application later.
As discussed earlier, the key differentiations of the premium Office 365 subscriptions come from the cloud services included. OneDrive will be familiar as Microsoft's cloud storage service, directly competing with Google Drive. Exchange provides email hosting with a 50GB mailbox and custom email domain address, accessible via Outlook for desktop or the Web version. SharePoint provides web-based collaboration including file sharing but also rapid creation of Web applications. Microsoft Teams integrates chat, video meetings, yet more cloud file storage, and integrated applications.
Microsoft Office 365 review: Verdict
Reviewing any version of Microsoft Office over the last decade has felt like a bit of a moot point, because its monopoly on business users is so huge that only a few companies are likely to make the switch. However, Microsoft appears to have headed off the main challenge from G Suite with the last few updates. The desktop software is undoubtedly more powerful than G Suite, and its collaboration integration is improving with every version, although it's not as intuitive as G Suite's just yet. Whilst companies might have considered using Google Drive for easy collaboration on top of Office desktop apps in the past, this is now very seamless with Office 365. It remains the gold standard of office software.
Verdict
Microsoft Office 365 provides an even more affordable route to the gold standard of office suites, with even more added value from online functionality.
Dr James Morris has worked as a technology journalist for over 25 years, including spending nine years on the staff of market-leading computer magazine PC Pro, the last five of which were as the publication’s editor. He specialises in enterprise-grade software and hardware, with a particular focus on content creation. He launched a pioneering video channel for HEXUS.net in 2006 and ran the video reviews channel for TrustedReviews.com for four years. He also runs a successful online digital content and commercial video production company, t-zero communications Ltd.
Dr Morris is a prolific technology writer and contributes commercial content for major IT brands including AMD, BlackBerry, Dell, Cognizant, HP, and IBM. He published a book on artificial intelligence, Can Computers Create Art? in 2009. He is also an academic, and is currently Pathway Director of the MA, Interactive Journalism at City, University of London.
Previously, he was course leader for the BA in Web Media Production at Ravensbourne University. He has a PhD in Philosophy, Art and Social Thought from the European Graduate School in Switzerland, a Master's in Media Arts from the New School in New York, USA, and a Bachelor's in Social Anthropology from the London School of Economics.
Dr. Morris can be found on Twitter at @Cyberwest, or emailed at j@tzero.co.uk