Hundreds of counterfeit shoe sites hit by Magecart credit card scam
Criminals hope to take advantage of those looking for a pre-Christmas deal

Customers seeking to grab a deal on top-end shoe brands this Christmas have been warned to avoid sites that promise heavily discounted prices as they risk being hit by a highly effective credit card scam.
A host of these websites, which try to exploit the rush by promoting counterfeit goods, have themselves been targetted by a large-scale hacking campaign that involves installing malicious scripts that lift financial information as it's entered, according to Malwarebytes.
The campaign is another example of the use of Magecart scripts, the same tactic used last year during a spate of attacks on high-profile websites, including those owned by Newegg, British Airways and Ticketmaster.
The tactic is now being used against sites that claim to promote goods from highly collectable brands such as Nike, Adidas and Converse, in some cases offering shoes worth over $1,000 for as little as $100 – all of which are counterfeit.
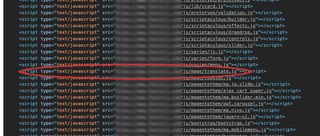
All affected sites were found to be loading a JavaScript file on their checkout page, a skimming script called translate.js, according to Malwarebytes, the final list of which highlights "a massive compromise across several IP subnets".
Some 288 sites have been identified, many of which are still in operation. In fact, we were able to access one such site and locate the Magecart script in action.

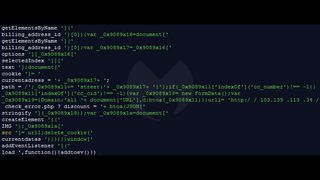
When deobfuscating the skimmer, researchers discovered that credit card data and billing addresses were being sent to 103.139.113[.]34, a server based in China. Investigations into several of the domains also revealed that they were all using the same outdated software, namely version 1.9.4.2 of Magento, and version 5.6.40 of PHP, suggesting that hackers simply used a scanner to crawl through the IP ranges and used the same vulnerability on each site.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
Skimming tactics of this kind are difficult to entirely stamp out, however, Malwarebytes has urged customers to keep their anti-virus software up to date, and to instal the browser extensions that normally come bundled.
The company also warned users to avoid sites that look like they haven't been updated in a while, particularly as many of these sites still display notes such as "Copyright 2015". Use of third-party payment services, such as PayPal, will also help reduce the need to manually enter card details into websites.
Dale Walker is the Managing Editor of ITPro, and its sibling sites CloudPro and ChannelPro. Dale has a keen interest in IT regulations, data protection, and cyber security. He spent a number of years reporting for ITPro from numerous domestic and international events, including IBM, Red Hat, Google, and has been a regular reporter for Microsoft's various yearly showcases, including Ignite.





