EU to fund bug bounties
Ethical hackers could earn up to $100,000 if they can spot vulnerabilities in the free open source software used by the European Union

The European Union (EU) has set up a bug bounty for 15 applications to help uncover security flaws in the most popular free and open source software on the web.
Bug bounties are a prize for people who actively search for security issues and the EU is calling on ethical hackers and developers to help find vulnerabilities in the open source projects it relies on.
The initiative was announced by Julia Reda, a member of the European Pirate Party and the co-founder of The Free and Open Source Software Audit Project (FOSSA), and will see the EU fund 15 bug bounties ranging from $30,000 to $100,000 depending on the software in question and the size of the vulnerability.
The FOSSA project started in 2014 to help improve the overall security of the internet after serious vulnerabilities were found. One of the issues found was in the Open Source encryption library OpenSSL.
"The issue made lots of people realise how important Free and Open Source Software is for the integrity and reliability of the Internet and other infrastructure," Reda said. "Like many other organisations, institutions like the European Parliament, the Council and the Commission build upon Free Software to run their websites and many other things.
"But the Internet is not only crucial to our economy and our administration. It is the infrastructure that runs our everyday lives. It is the means we use to retrieve information and to be politically active."
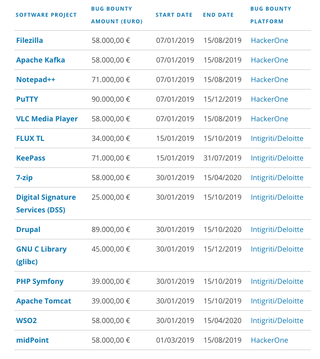
A list of the open source projects - courtesy of Julia Reda's EU profile page
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
In January the European Commission will launch 14 out of the total 15 bug bounties on free software projects that the EU institutions rely on. The software projects chosen include Filezilla, Apache Kafka and Drupal and were identified as candidates during a public survey.
Bobby Hellard is ITPro's Reviews Editor and has worked on CloudPro and ChannelPro since 2018. In his time at ITPro, Bobby has covered stories for all the major technology companies, such as Apple, Microsoft, Amazon and Facebook, and regularly attends industry-leading events such as AWS Re:Invent and Google Cloud Next.
Bobby mainly covers hardware reviews, but you will also recognize him as the face of many of our video reviews of laptops and smartphones.
Most Popular






