Thomas Cook phishing sites skyrocket following firm's collapse
Former employees and customers are believed to be the targets of malicious campaigns capitalising on the company's liquidation

Security researchers have detected 53 Thomas Cook-related domains having been registered in the week after the travel operator went into receivership, a sharp rise from the norm.
Skurio's researchers issued an alert to former employees and customers of Thomas Cook calling for greater vigilance when visiting online services claiming to be associated with the fallen travel company.
The researchers told reporters at a media event that some of the domains were registered with good or harmless intent, but it seemed as though a minority were created for phishing purposes.
Patrick Martin, head of threat intelligence at Skurio said as of 1 October, as far as he could see, none of the sites were actively hosting malware, "but there's 53 domains out there so I'd be surprised if at least one or more [wasn't]".
"With the majority of the ones I looked up, malware wasn't the game, it was more about harvesting user data," added analyst John Evans. Below is a screenshot of one of the new sites and the form it asks users to complete.
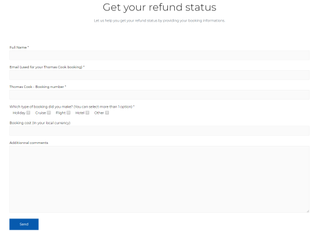
Martin added that roughly 25% of the domains were simply piggybacking off the collapse and used as harmless redirects to other sites one redirected to a UK license plate website.
Others were simply using the domain to get clicks on adverts, according to Evans. "There were quite a few I bumped into though that were just capitalising on ad revenue. There was one that was like, how to help Thomas Cook holidaymakers, so if you want to book a new holiday or find jobs for Thomas Cook employees all it's doing is, when you click on it, it takes you straight to Expedia, or wherever."
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
"One of them is German, it was a .de domain which took you to a German page," said Martin. "It was just two lawyers talking about Thomas Cook and their subsidiaries." The site pretends to be a legitimate business using the Thomas Cook likeness to make money from customer refund claims.
Around 50% of the domains had holding pages, like stock home pages, given to websites using platforms such as Wix or WordPress as they waited for the full site to go live.
The small remaining portion had no landing page at all which, according to the researchers, could indicate that the domain was registered so phishing attempts could be made on former employees and customers from a legitimate-looking email address.

6 best practices for escaping ransomware
A complete guide to tackling ransomware attacks
Skurio's team were monitoring the state of Thomas Cook-related sites for over a year, long before it first became apparent the company was in trouble - supporting them as it would any other client. Its researchers said roughly one-to-two sites using the Thomas Cook name were consistently, like a flatline, being registered per fortnight prior to the company's issues which illustrates the extreme rise following the company's demise.
"So that flatline turned into this spike and nearly every day subsequent to that, roughly eight per day [being registered]," said Martin.
UK citizens may have already been alerted to the influx of Thomas Cook-related scams already as banks have been quick to issue alerts to customers warning against the rise in threats targeting them.
Users of the Co-operative's mobile banking app are being presented with an alert on logging in, saying: "Criminals are taking advantage of people impacted by the news that Thomas Cook have ceased trading. Never give out your bank account or card details to anybody that contacts you out of the blue".

The company also added a fraud prevention statement to its website on the day Thomas Cook announced its liquidation, as did Santander and HSBC.
Those affected by the collapse should contact the CAA in the first instance, which will be able to offer guidance on what to do next.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.




