Malware
Latest about Malware

How computer viruses spread and how to avoid them
By Tyler Omoth, Bobby Hellard last updated
In-depth You know that computer viruses can be a nightmare; here's how they spread from one computer to the next

Researchers uncover novel RDStealer malware targeting remote desktop protocol
By Richard Speed published
News Bitdefender's experts said the level of disguise observed in this campaign “surpasses anything witnessed thus far”

The top malware and ransomware threats for June 2023
By Connor Jones published
News Organizations face a fresh round of cyber threats as criminals continue to evolve their tactics

Kaspersky traces spyware attack on staff iOS devices back to 2019
By Rory Bathgate published
It's currently unclear who is behind the spyware attack on the Russian-based cyber security firm
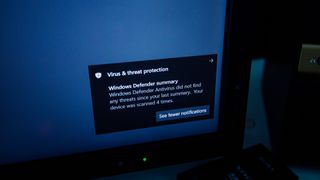
How to turn on Windows Defender
By Connor Jones last updated
In-depth A simple guide on how to turn on Windows Defender in Windows 10 and Windows 11, and turn it off again if necessary

US reveals bespoke tool that took down Russian malware operation
By Rory Bathgate published
News Snake had been used to steal NATO countries’ data for 20 years

Security awareness training strategies for account takeover protection
By ITPro published
Whitepaper Why you need an inside-the-perimeter strategy for internal threats

New Domino Backdoor malware linked to ex-Conti, FIN7 criminals
By Rory Bathgate published
News Evidence suggests that gang members have teamed up, researchers warned
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.




