And then there's SmartView Tracker for perusing raw log data for all blades plus SmartLog which offers log management and search facilities for all top activities.
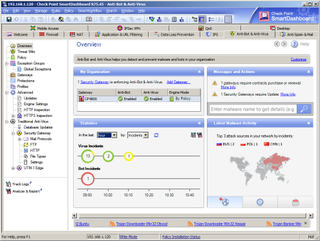
The new anti-bot blade works with the anti-virus and anti-spam blades to provide extra layers of malware protection.
Software blades
A feature of Check Point's appliances that makes them easy to customise is their software blades. The firewall blade is the foundation for all Check Point appliances and defaults to blocking all traffic. You create firewall rules by defining network objects, services, users and groups in the left pane, dragging them directly into the relevant rule and applying an action.
The new Gaia interface is a welcome update although the number of management and monitoring tools will take a while to get to grips with and can increase costs further.
The URL filtering blade uses Check Point's AppWiki feature which provides a database of Web 2.0 apps, options for controlling specific Facebook activities and a list of around 250,000 social network widgets. During testing we found it worked well with very few dodgy web sites getting past its defences.
The identity awareness blade links user names to systems so security policies can be applied to user identities regardless of where they log in from. BYOD users can be controlled with the mobile access blade which provides secure portals for mobile devices accessing corporate resources.
The new anti-bot blade teams up with the anti-virus and anti-spam blades to provide internal protection against malware. Using Check Point's new ThreatCloud service it can detect and block bot-infected systems, prevent further infections and use forensics to provide detailed activity logging.
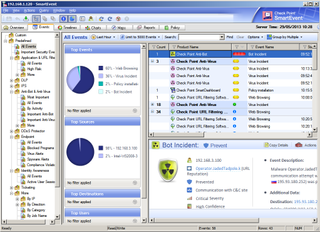
The optional SmartEvent provides detailed graphical reports on security events and blade activity.
Turnkey models
The 4800 Appliance is available in four models. The base NGFW (Next Generation Firewall) model runs the firewall, IPsec VPNs, mobile access licensed for five users, clustering, identity awareness, IPS and application control blades and costs around 17,000 ex VAT for the first year.
The NGTP (Threat Prevention) model adds the URL filtering, anti-bot, anti-virus, email security and IPS blades and costs approximately 20,500 for the appliance and a one year subscription.
Costs can increase substantially if you're not careful. The NGDP (data protection) model adds DLP to the firewall model but if you want this blade separately it'll cost an additional 4,000 for a one year subscription.
Some reporting tools are optional extras as well. For example, the SmartEvent and SmartReporter bundle for sites with up to ten security gateways incurs a one-off cost of around 5,500.
Conclusion
Check Point's new 4800 Appliance offers a comprehensive package of security measures that can be customised to suit with a range of software blades. The new Gaia interface is a welcome update although the number of management and monitoring tools will take a while to get to grips with and can increase costs further.
Verdict
The 4800 Appliance delivers a superb range of data security measures and the new Gaia web interface simplifies deployment immensely. Check Point’s software blades allow you to pick and choose which features you want although some optional reporting tools are expensive.
Chassis: 1U rack Memory: 4GB (max 8GB) Network: 8 x Gigabit Storage: 250GB SATA hard disk Ports: 2 x USB, RJ-45 console Expansion: Slot for optional Gigabit network modules Management: Web browser, CLI, SmartConsole Suite
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.


