Stopping automated attacks with shapeshifting websites
How we can defend against automated attacks? Tom Brewster takes a look...

A moving target is always harder to hit than a stationary one. IT security types have exploited this fact for years, but never before has a service come along that shifts around the high-level of a website's code to thwart attacks.
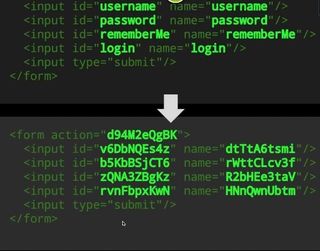
But that's what the geniuses at Shape Security, who have histories at Google and the US Department of Defense, have done. After two years of development, they've found a way to alter HTML, CSS and JavaScript code without altering the user experience. The algorithms figure out fresh ways to do that with every webpage visit. The ultimate idea of this polymorphism is to stop automated tools probing for predictable weaknesses, as they won't be able to detect them if the structure of the site is scrambled on each request.
This is big. If the major banks apply this kind of technology, it will significantly weaken the majority of banking malware out there. It's no surprise the company's first customers are in the financial industry.
Shuman Ghosemajumder, vice president of strategy at Shape, explains how this actually helps: "What this means is that it now becomes difficult or even impossible to be able to script an attack against the application because it is no longer reliably static. [An attacker] won't know how to get their code to interact with the web application's code anymore."
Automated vulnerability scanners will have no hope against these shapeshifting sites and application layer distributed denial of service attacks should be limited by the technology too. But where I see this technology being really valuable is in the banking sector.
Prevalent financial man-in-the-browser malware like Zeus has long caused issues for banks, costing the millions upon millions of pounds over recent years. Such malware contain scripts that automatically out commands on bank websites as the customer visits them, initiating transactions silently. "What we do is prevent the Trojan from successfully being able to send commands to the banks website anymore," Ghosemajumder notes.
HTML web injects, where the malware replaces pieces of the bank's website, such as the login form, would be impossible too. Any attempt to inject code in this way would corrupt the page "pretty horrendously," Ghosemajumder adds.
This is big. If the major banks apply this kind of technology, it will significantly weaken the majority of banking malware out there. It's no surprise the company's first customers are in the financial industry.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
Tom Brewster is currently an associate editor at Forbes and an award-winning journalist who covers cyber security, surveillance, and privacy. Starting his career at ITPro as a staff writer and working up to a senior staff writer role, Tom has been covering the tech industry for more than ten years and is considered one of the leading journalists in his specialism.
He is a proud alum of the University of Sheffield where he secured an undergraduate degree in English Literature before undertaking a certification from General Assembly in web development.





