Identify yourself
After grouping our ports, we applied firewall rules to source and destination zones along with associated networks and hosts. Other network objects include service filters, blocking actions and time schedules which can be applied within each rule.
We recommend acquainting yourself with Cyberoam's identity-based security as this allows you to apply more versatile security policies to users and groups. Clients authenticating to an external directory server will be automatically logged in while others can log in to the appliance via the Corporate Client.
Cyberoam provides Linux and Mac clients plus free mobile apps for Android and iOS devices. We had no problems with the iAccess app on our iPad where it auto-detected the appliance's IP address and asked for our login details.
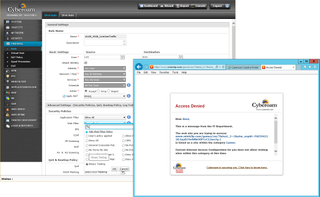
Cyberoam's web filtering can be applied to specific users and performs extremely well
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.



