Virginia shooting - don't open that link!
Scammers and cyber criminals love to capitalise on tragedy, and we can't help but click
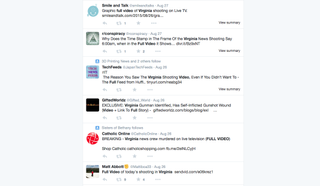
Shootings in America are, sadly, not unusual, but when two journalists were shot live on air on Wednesday last week, social media went into overdrive.
What made this particular attack unique is the fact it was filmed and broadcast by the victims as it happened and, it later transpired, the shooter himself had recorded the murder and posted it online before taking his own life.
Very quickly, my Twitter feed was full tweets from news organisations such as the Huffington Post linking to stories containing the "graphic footage" or, in the case of Russia Today, having a short Vine of two people dying auto-play when you scrolled down.
Soon though, news outlets reacted to the revulsion people expressed at their decision to rebroadcast the footage and removed it from their stories. Facebook and YouTube were also diligent in their efforts to remove the footage taken by shooter Vester Lee Flanagan as it was posted and reposted.
But, for some, the desire to see the footage first hand is too much, and cyber criminals know this as much as - or perhaps better than - anyone else.
By the evening, the Virginia trend on Twitter was full of rather suspicious-looking links to the "full uncensored video".
Social engineering attacks that take advantage of our curiosity are among the most successful at attracting victims and are also relatively easy to create, which is why they remain so popular with cyber criminals as a vector of attack.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
It's not just social media, either - emails are still circulated in the wake of tragedies, be it a link to an alleged miracle survival video from a natural disaster or something more grisly, as in this case.
"Malicious actors are always going to use something that's in the media to try and lure in victims," Tim Grieveson, HP's chief cyber and security strategist, told IT Pro. "We're human, we are voyeurs, and they know that."
"To protect against successful attacks, you need to have good technology in place, but it's also about educating people to be careful, both in the business and at home. There are still a lot of people who get caught out by phishing emails - they still click that link - but education now has to be mulit-platform and include social media as well," Grieveson said.
Even though there's a strong moral argument against it, curiousity will always get the better of some people - they want to feel hope in the face of disaster, they want to feel righteous anger when ISIS execute a prisoner, they want to see something ususual and shocking.
But, just maybe the threat of malware, rather than a salacious video, will make us think twice in future.

Jane McCallion is ITPro's deputy editor, specializing in cloud computing, cyber security, data centers and enterprise IT infrastructure. Before becoming Deputy Editor, she held the role of Features Editor, managing a pool of freelance and internal writers, while continuing to specialise in enterprise IT infrastructure, and business strategy.
Prior to joining ITPro, Jane was a freelance business journalist writing as both Jane McCallion and Jane Bordenave for titles such as European CEO, World Finance, and Business Excellence Magazine.




