Strider spying group targets Russia, China, Belgium and Sweden
Strider spying collective hacks an eclectic mix of victims
A secretive spying collective that appears to like Lord of the Rings has attacked an embassy in Belgium and a China airline, among other targets.
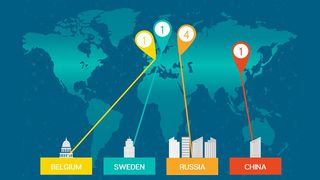
Security firm Symantec only recently discovered the stealthy group, dubbed Strider, after finding it has targeted a select number of organisations in China, Russia, Belgium and Sweden over the past five years.
Symantec described the Strider group as "highly selective" and has only found evidence of 36 infections, which affected just seven targets. The majority of these were individuals and organisations in Russia, but also included an airline in China, an organisation in Sweden and an embassy in Belgium.
The attacks are executed using a piece of sophisticated malware known as Remsec, which Symantec described as "a stealthy tool that appears to be primarily designed for spying purposes including a keylogger, network listener, a basic and an advanced pipe back door, and an HTTP back door".
One unique quirk the researchers did discover in the keylogger module's code, however, is a reference to Sauron, the primary antagonist in the Lord of the Rings saga, who appears in the series as a single all-seeing eye. This is, presumably, a joke on the part of the creators, given the module's capability to spy on every keystroke made on the infected computer.
Symantec did not name the targets, nor which nation the embassy in Belgium represented, but said in a blog post: "The [group's] ... targets have been mainly organisations and individuals that would be of interest to a nation state's intelligence services."
The security firm has also declined to speculate as to which nation state could be the originator of the attacks, but said it will continue to search for more Remsec modules and targets in order to increase its understanding of Strider's operations.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.

Jane McCallion is ITPro's deputy editor, specializing in cloud computing, cyber security, data centers and enterprise IT infrastructure. Before becoming Deputy Editor, she held the role of Features Editor, managing a pool of freelance and internal writers, while continuing to specialise in enterprise IT infrastructure, and business strategy.
Prior to joining ITPro, Jane was a freelance business journalist writing as both Jane McCallion and Jane Bordenave for titles such as European CEO, World Finance, and Business Excellence Magazine.




