How to check if you've been hacked
Find out how to check if your account has been hacked
Another week, another major hack. It seems like cybercriminals are dumping our account details faster than we can keep up this week's victim is Yahoo, but there's few online services that haven't been hit.
That's worrisome for those of us using these online services, especially those of us with a bad habit of reusing passwords (we'll get to that).
Here, we'll reveal how to find out if your account logins are up for sale online and what to do about it if they are.
Why is it worth checking?
In the past year alone, hundreds of millions of account details have been leaked online.
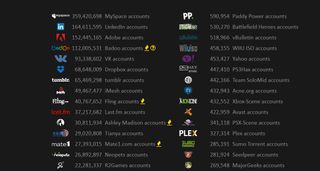
Back in May, MySpace remember them? admitted as many as 360 million accounts were at risk after a breach of emails, passwords and usernames, with LinkedIn losing details of 117 million accounts to the same hacker. Peace, as he or she or they charmingly goes by, is also thought to be behind the dump of hundreds of millions of Yahoo credentials. Busy little bee, is Peace.
Tumblr also took a tumble, leaking 65.5 million account details, and though Twitter claimed in June it wasn't hacked, it still managed to expose 32 million passwords. And another hacker sold nearly 300 million logins from Gmail, Hotmail, Yahoo and Mail.ru, though many were out of date.
The list goes on and on. Hackers are paying attention to your login credentials, and that means so should you.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
How to check if you've been hit
There's several websites that let you enter in your username or email address to see if there's any leaked login details matching them.
A warning, though: these sites check data that's been dumped online or been bought by clever researchers. If a hacker has your credentials and intends to use them, they won't immediately be revealed online, so such sites can only help so much.
That said, it's a start and often quite the wake-up call.
One to try is Have I Been Pwned, from security researcher Troy Hunt. Simply drop your email address or login name into the box and hit enter to see if your details are listed from breaches of 142 websites.
If your details are found in the data dumps, you'll get a terrifying red message detailing exactly what was taken in each hack. You'll want to change your password if you haven't already, and change any where you used the same password across multiple accounts.
If you're not listed, you'll get a green message with the good news. That doesn't mean your account hasn't been hacked, however it only means you weren't hit by the hacks that Hunt lists.
There's also an option to subscribe to get a warning if your details turn up in future breaches and in "sensitive" data dumps. To search those, Hunt requires verification that you're the owner of the email, otherwise you could enter your partner's email address and find out that they were hit by the Ashley Madison or YouPorn attacks. That could be awkward for some.
That means signing up for notifications not only gives you a warning system in case your accounts are hacked in the future, but also means your details are also run through the "sensitive" data dumps so it's worth taking the extra step.
There are other sites that do a similar job. Hacked Emails is similar to Have I Been Pwned, though it isn't quite as thorough as Hunt's site (it missed one of the leaked lots one of my emails is in). Handily, it has a Chrome Extension that alerts you if anyone sending you email has been hacked, and may be compromised.
BreachAlarm is similar to Have I Been Pwned, but doesn't tell you the specific account that's been hacked, which isn't very useful. That means you need to change any account associated with that email address, which may well be a lot.
Pay attention
There's another way to spot if your accounts have been hacked: pay attention. If a web service or site sends you an email begging you to change your password or nags you with a pop up to do the same, then listen and obey.
Others will warn you of odd behaviour, with Gmail and Chrome showing a notification of a new login. If that wasn't you, assume you've been hacked.
Of course, not all companies are keen to let you know when they've been hacked. Sony, eBay, we're looking at you. Sometimes that leaves the rest of us out of the loop, but other times such breaches make the headlines before the company is willing to own up or can even confirm the attack themselves -- that appears to be what's happened with Yahoo. In that case, the hacker leaked 200 million credentials in August, but Yahoo is only expected to confirm the incident this week, a month later.
In short, if you read about the Yahoo leak in August, you should have refreshed your password in August. Don't wait for official confirmation first.
How to stay secure
Whenever there's a big security breach, researchers and experts pipe up with their advice for staying secure online, and it normally runs the same.
Every now and then, change your passwords. Much of the leaked data is years' old more often than not, a twice-annual refresh means you'd be secure even if you password was on the list.
Have different passwords for different sites, so hackers can't try one leaked credential against another site and get access.
Turn on two-step (or two-factor) authentication. Good web services offer this extra layer of security for a reason, so use it.
None of this guarantees your credentials won't be swiped or that access to your account won't be gained by criminals, but it does help make it less likely. And that's really the best we can hope for.




