LinkedIn exploit 'left millions exposed' to malware
Check Point research highlights now patched vulnerabilities in LinkedIn's messaging service

Exploits in LinkedIn's own security measures potentially allowed hackers to spread malicious files across the social networking site and infect millions of user PCs, it has been claimed.
The Microsoft-owned professional networking site, that boasts over 500 million users in 200 countries, allows members to chat, share CVs and send job descriptions to others in their network using a messenger service.
Multiple vulnerabilities were identified in LinkedIn's own security measures that are designed to restrict the types of files that are uploaded to LinkedIn's chat windows, according to security researchers at Check Point.
Typically these measures allow only a handful of extensions including pdf, text documents and jpegs, however, it was discovered that attackers could bypass these checks by uploading malicious files masquerading as accepted extensions. These were then capable of spreading throughout a user's network of contacts and infect any PCs connecting to those accounts.
The research identified four exploits in the LinkedIn security systems, including a limitation that failed to identify a malicious Power Shell script that was saved as a .pdf, which if downloaded, would remain undetected on a user's PC.
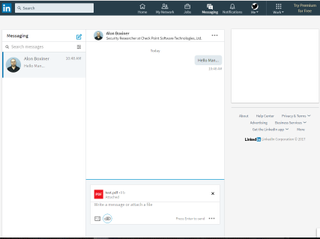
How a link may have appeared in a user's chat window
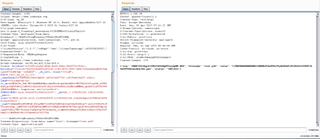
The Power Shell script made to masquerade as a .pdf file
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
The system was also unable to detect malicious Excel XLSM macros, disguised with an accepted .xlsx extension, which when uploaded would bypass the antivirus checks and be sent unnoticed to a user.
These types of attacks meant hackers could infect a user's PC with whatever code they wished, potentially stealing personal information, encrypting data, or hijack a machine for the purpose of spreading malware to other PCs.
Although there is no evidence that the vulnerabilities had been noticed and exploited by hackers, it serves to highlight the importance of robust security measures on a site that allows its millions of users to share files with each other.
Check Point notified LinkedIn of the vulnerabilities earlier this year, and they have since been acknowledged and patched as of the 24 June.
Main image: Bigstock - body images courtesy of Check Point.
Dale Walker is the Managing Editor of ITPro, and its sibling sites CloudPro and ChannelPro. Dale has a keen interest in IT regulations, data protection, and cyber security. He spent a number of years reporting for ITPro from numerous domestic and international events, including IBM, Red Hat, Google, and has been a regular reporter for Microsoft's various yearly showcases, including Ignite.





