Box developing AI to hunt for data breaches
Box Shield will monitor all file activity, making it easier to spot leaks
Cloud content management firm Box is working on a machine learning-based security platform to give admins a detailed overview of a company's content and provide early warnings of potential data breaches.
Box Shield, which is currently in preview stage, is being built to sit on top of the company's existing portfolio of products, allowing security analysts to check to see what content is being accessed, who is accessing it, and whether sensitive data is being downloaded.
One of its main features is its artificial intellignce layer, which is being trained to categorise employees based on their activities, and flag to admins if any unusual behaviour was discovered.
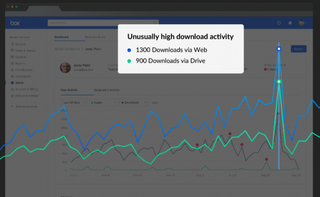
Each employee's activity history is monitored, including where and how they access files
Revealing the platform at its annual Box Works conference in San Francisco this week, the company explained that the system is designed to prevent employees from accessing data they shouldn't and to identify those accounts that may have been compromised.
In an example shown on stage, the system is capable of building profiles of employees, for example, sales team members, and alert IT teams if such users attempt to access content belonging to another, unrelated team, such as engineering.
Similarly, the system is also capable of spotting breached accounts by analysing the location of a recent login and assessing whether it was possible for that employee to have travelled to that area since their last activity.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
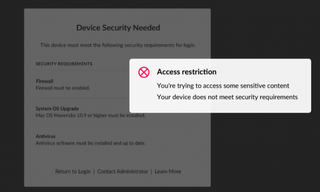
Access policies can be set on a file-per-file basis, whether being accessed internally or externally
Box claims the system solves the problem of keeping track of both internal and external users accessing content within an organisation, particularly as there's no guarantee they are using secure or a managed device.
"Collaboration is happening at an accelerated pace," said Jon Fan, vice president of product management at Box. "We have more people working on our content, and it's not only just our employees, it's the employees of our partners, our vendors, or suppliers... but even more so now it's including things like our contractors.
"So we no longer have purely internal or purely external users in our organisation. This makes it really difficult to protect our data."
Box said it's also building in an enhanced firewall that offers a more robust version of two-factor authentication, that not only verifies a login but also checks to see whether the account is genuine.
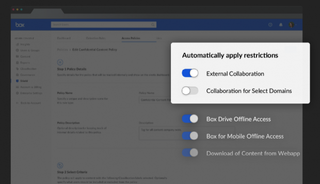
Security policies can be adjusted on the fly, and assigned to specific documents
Another major feature is the ability to create focused security policies that can be applied universally at the content level. Based on the demo shown on stage, this essentially works in the same way as tagging emails, where you can assign a predefined policy to a file or folder on the fly.
These policies can be built within the Box Shield dashboard, allowing admins to define whether a policy lets users download content for offline use, or share content beyond their organisation. This also means that policies already applied to documents can be adjusted over time, such as adding or removing approved users.
A beta version of Box Shield is planned for later in the year, however, the company gave no indication as to when it plans to release the product generally, or how much it will cost.
Dale Walker is the Managing Editor of ITPro, and its sibling sites CloudPro and ChannelPro. Dale has a keen interest in IT regulations, data protection, and cyber security. He spent a number of years reporting for ITPro from numerous domestic and international events, including IBM, Red Hat, Google, and has been a regular reporter for Microsoft's various yearly showcases, including Ignite.





