US military weapons systems found to have vulnerabilities
Department of Defence "did not prioritise weapon system security", claims report

The trillion-dollar arsenal of advanced weaponry the United States Military owns has been found to have "mission-critical cyber vulnerabilities", according to a report.
Published by the US Government Accountability Office (GOA) the report claims that the US Department of Defence (DOD) had not prioritised cybersecurity when building its advanced weapon systems.
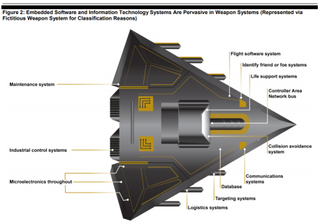
Graphic of an automated weapon - courtesy of the GOA
"Automation and connectivity are fundamental enablers of DOD's modern military capabilities," the report said. "However, they make weapon systems more vulnerable to cyber attacks.
"Although GAO and others have warned of cyber risks for decades, until recently, DOD did not prioritise weapon systems cybersecurity. Finally, DOD is still determining how best to address weapon systems cybersecurity."
The DOD is said to be planning to spend an estimated $1.66 trillion to further develop its current portfolio of major weapons and the GOA had been asked to review the state its current weapons system security.
In operational testing, the GOA found mission-critical cyber vulnerabilities in systems that were under development that program official believed were secure - some even discounted the test results as "unrealistic".
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
Worryingly, very simple tools and techniques were used to take control of the systems and went largely undetected. Basic issues such as poor password management and unencrypted communications were just some of the vulnerabilities found.
According to the report, the DOD is taking steps to improve its weapon system cybersecurity, which includes issuing and revising policy and guidance, but its remedial work will need to be swift as cyber threats are becoming more advanced.
In August, researchers at Rutgers University revealed that a normal Wi-Fi network could be used to detect weapons, such as firearms, bombs and explosive chemicals and in July, it was revealed that a hacker infiltrated the Air Force and stole files pertaining to a lethal drone, which later leaked onto the dark web.
"It is shocking to find out critical systems especially weapons systems are still using default vendor passwords," said Joseph Carson, chief security scientist at Thycotic. "This report's findings reveal that anyone in the world with sufficient cybersecurity skills could be in control of the worlds most advanced weapon systems within hours."
Bobby Hellard is ITPro's Reviews Editor and has worked on CloudPro and ChannelPro since 2018. In his time at ITPro, Bobby has covered stories for all the major technology companies, such as Apple, Microsoft, Amazon and Facebook, and regularly attends industry-leading events such as AWS Re:Invent and Google Cloud Next.
Bobby mainly covers hardware reviews, but you will also recognize him as the face of many of our video reviews of laptops and smartphones.





