Two-thirds of hotel websites leak personal data
Confirmation emails are inadvertently sharing booking details with third-party advertisers
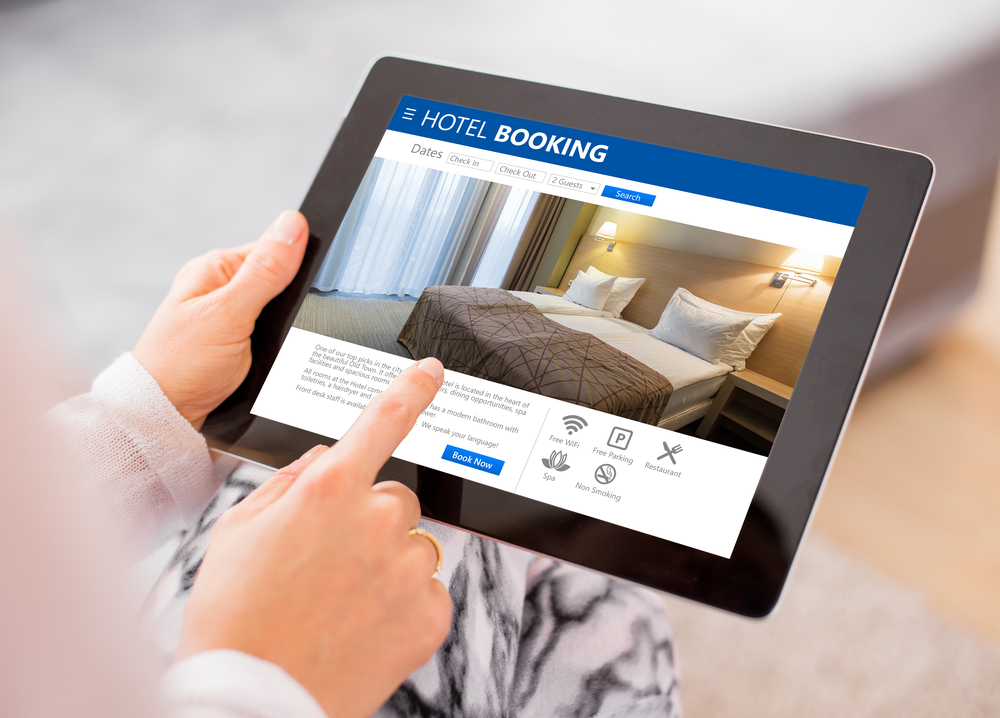

Two-thirds of hotel websites inadvertently leak personal data to third-party companies and leave customers vulnerable to hackers.
This is according to research from cyber security firm Symantec, which found that the majority of booking systems used by hotels could allow scammers to access information such as mobile phone and passport numbers.
The leaks come from confirmation emails, sent to customers often containing an unsecured direct link to their booking. The report suggests that anyone on the same network could intercept the email and modify or cancel their reservation.
Principal threat researcher, Candid Wueest, tested the websites of 1,500 hotels from 54 countries and found that two in three of them, or 67%, had the problem. The security lapses are in breach of the EU's GDPR laws, which state that firms must protect the personal data of customers.
"The fact that this issue exists, despite the GDPR coming into effect in Europe almost one year ago, suggests that the GDPR's implementation has not completely addressed how organisations respond to data leakage," said Wueest.
Of the websites Wueest tested, more than half (57%) send confirmation emails to customers with a direct access link to their booking. This is for the convenience of the customer, giving them a simple link to click straight into their reservation without having to log in.
Because these emails require a static link, the booking reference code and the email are sent in the URL itself. This wouldn't be a problem on its own, but most of the websites load additional content on the same website, such as advertisements, meaning that the direct access is shared, either directly with other resources or indirectly through the referrer field in the HTTP request.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
There are other scenarios in which the booking data may also be leaked. Some sites pass on the information during the booking process, while others leak it when the customer manually logs into the website. In most cases, Wueest found that the booking data remained visible, even if the reservation has been cancelled, offering up a large window of opportunity for hackers to steal personal information.
There were a number of hotel chains suffering data breaches in 2018, such as the Radisson chain, which had its customer's details accessed via its rewards scheme, and Mariott's Starwood Hotel system, which saw a major flaw discovered in its reservation system.
Bobby Hellard is ITPro's Reviews Editor and has worked on CloudPro and ChannelPro since 2018. In his time at ITPro, Bobby has covered stories for all the major technology companies, such as Apple, Microsoft, Amazon and Facebook, and regularly attends industry-leading events such as AWS Re:Invent and Google Cloud Next.
Bobby mainly covers hardware reviews, but you will also recognize him as the face of many of our video reviews of laptops and smartphones.
-
 CISO warns agentic AI tied to major risks and failure
CISO warns agentic AI tied to major risks and failureNews Runtime security and employee oversight are necessary to achieve success with AI agents, according to Haider Pasha
-
 Enterprise browsers: the new standard for security?
Enterprise browsers: the new standard for security?In-depth The market for enterprise browsers is growing fast – but are their features and security controls enough to compete with free applications?
