This tool can work out how often your company will be hit by insider attacks
Size, sector and employee welfare all used as factors of email-based intrusion

Organisations in the process of assessing their cyber security defences have been given a new tool that claims to calculate the risk of sustaining an email-based attack.
The Insider Breach Calculator, launched today by Egress, calculates how many potential breaches a business may expect to sustain by feeding factors such as employee email habits and mood into an algorithm. These factors include the number of employee inboxes and the industry they work, as well as the perceived stress level and fatigue level of workers between zero and ten.
When the figures are plugged in, the results are tallied and presented as the estimated number of emails sent per week and per year, and how many potential breaches an organisation may sustain during those periods.
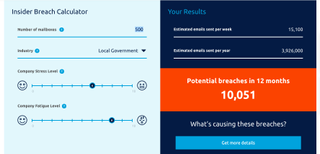
This fictional local government agency with 500 mailboxes could face over 10,000 incidents per year
These results can then be broken down by the proportion of accidental versus malicious incidents, as well as the leading potential causes for each category. The explanations provided span employees clicking on a malicious phishing link to employees sharing data to personal systems.
"Every organisation knows that it is leaking data in one way or another, yet we find there is a bit of a 'head-in-the-sand' mentality where the insider breach is concerned," said Egress CTO Neil Larkins.
"With an average of 60 emails sent every day by one individual within an organisation, the chances of employees accidentally leaking data, continues to grow exponentially. This is before we even consider intentional and malicious leaks, as well as 'forced errors' caused by sophisticated phishing attacks.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
Based on calculations, a small business in the telecoms sector with 100 employees that are moderately fatigued and stressed (five out of ten) could suffer as many as 5,288 potential breaches in 12 months.
When broken down further, the most likely cause of an accidental breach is employees unaware of information that shouldn't be shared, while the most likely cause of a malicious breach would be employees leaking data to a competitor.
A large telecoms business of 2,000 employees under the same pressures, by contrast, would suffer more than 35,000 potential breaches within 12 months.
Meanwhile, a hypothetical NHS organisation with 6,000 employees under maximum stress and fatigue will likely suffer 131,914 potential breaches in just one year, equivalent to 361 breaches per day. The weight placed on employee welfare is significant, with the same workplace sustaining only 94,224 potential breaches when its hypothetical staff are under no stress or fatigue.
Research has shown that one of the biggest factors in cyber risk are employee-based intrusions, with 89% of risks now internal. Moreover, 48% of businesses will experience at least one security incident each year as a result of unintentional employee action.

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.




