EA hackers steal source code for FIFA, Battlefield game series
Stolen data has now been posted for sale on the dark web

Hackers have downloaded approximately 780GB of data from video games publisher Electronic Arts (EA) and are in the process of selling portions of the cache to buyers on the dark web.
The publisher, which manages popular series such as FIFA, Battlefield, and The Sims, said in a statement that a limited amount of game source code and internal tools were stolen, according to Motherboard.
The cyber criminals responsible are now actively selling portions of the stolen data through the dark web, according to screenshots seen by the publication, and are seeking serious buyers.
EA has said that the incident did not involve ransomware, but the company is yet to detail how the hack unfolded.
Other stolen data includes source code and tools for the Frostbite gaming development engine, proprietary EA frameworks, and software development kits (SDKs), with the compromised cache totalling roughly 780GB.
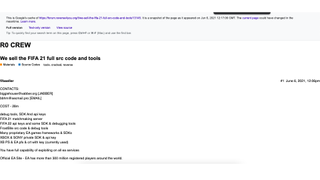
A cached web page dated 6 June suggests buyers can attain "full capability of exploiting on all ea services" for the cost of "28m". The post also claims to have taken charge of the FIFA 21 matchmaking server and FIFA 22 API keys. The cyber criminals also provided samples of the stolen information.
"We are investigating a recent incident of intrusion into our network where a limited amount of game source code and related tools were stolen," an EA spokesperson told Motherboard and other publications in a statement.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
"No player data was accessed, and we have no reason to believe there is any risk to player privacy. Following the incident, we've already made security improvements and do not expect an impact on our games or our business. We are actively working with law enforcement officials and other experts as part of this ongoing criminal investigation."
IT Pro has asked EA to clarify the nature of the attack, and confirm whether or not it was a ransomware incident.
EA is the latest gaming company to be hit in a cyber attack after the Polish developer CD Projekt was compromised in February this year.
Hackers stole company data as well as encrypted a number of developer devices in a ransomware attack, before subsequently auctioning off stolen assets in a self-described "charity fundraising" exercise.
Although hackers are selling off portions of the data they seized, cyber security specialist with ESET, Jake Moore, suggested the attack likely wasn't financially motivated.

IT Pro 20/20: What the EU's new AI rules mean for business
The 17th issue of IT Pro 20/20 considers the effect of new regulations on the IT industry
"Attacks on games publishers are usually for other reasons such as cheat making or underground community kudos," he said. "Gaming source code makes a popular target for cheat makers and their communities, so protection must be water tight.
"There will be an inevitable indirect financial hit as EA recovers from a frustrating strike, but luckily this is not related to ransomware like many other current targeted cyberattacks delivering a two-pronged attack."
Challenged on why the hackers are seeking buyers for the stolen data if it isn't financially motivated, Moore added: "Of course malicious actors can attempt to profit from any attack when it suits them".
"It is common for games publishers to have their data stolen purely for cheat makers," he continued, "but if this comes at a time when such data is seen to have a greater value than normal, the attackers have possibly noted this change in demand and decided to profit from it."

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.




