The guide to mobile security
Going mobile brings a host of benefits, but you need to be careful with your data.

When business computers were exclusively standalone units tied to the desk, keeping the digital work environment secure was mostly a matter of ensuring the premises were physically locked. But the workplace is increasingly a mobile environment, with notebooks replacing desktops, and with tablets and smartphones proliferating. This flexibility means employees can now work at any time and in any place. But it also makes the issue of keeping business data secure many times more complicated. The devices themselves could be stolen, and important business information may well be travelling over public networks, where it could be snooped upon. In this feature, we will look at ways you can keep your employees' mobile devices as secure as possible.
One of the biggest security issues of the mobile revolution is what is known as Bring Your Own Device (BYOD), where employees can take their own tablets, smartphones and laptops into the workplace. The upside is that employees get to use a device that they are familiar with, and have chosen, rather than the company standard. For example, they might want to work on an iPad instead of a laptop, or use the latest smartphone. But these devices will naturally not be part of the standard company security policy. This is part of the strategy behind Windows 8, with some Windows 8 tablets offering an experience pleasant enough to be an alternative to other tablet brands. But they can be brought under the same security policies as Windows 8 laptops and desktops.
Whether or not you manage convince employees to stick with a uniform platform, losing a mobile device, or having it stolen, can mean important business data will fall into someone else's hands. So the most obvious first step is to ensure that every mobile device is at least protected with a password, or with a lock code, depending on capability. Good password and passcode practice should be applied, such as avoiding '1234' as a phone PIN. A corporate-grade notebook with built-in biometric security, usually a fingerprint reader, will improve security considerably, as this provides a login that is much harder to crack than a mere text password. With Intel-based notebooks, the password will be stored in a secure hardware chip called the Trusted Platform Module (TPM).

Windows' NTFS also supports encrypted folders. It's a simple checkbox option in the Advanced options of the General tab in a Windows folder's Properties. Once enabled, a user will see no difference to the behaviour of their computer. But these folders will now be encrypted, so even if the storage device is removed and analysed with another system, the contents of the encrypted folders will remain secure. Only when the correct user is properly logged in will these folders be readable. Of course, this also means greater care needs to be taken to keep a secure record of keys and passwords, so the encryption doesn't keep your users away from their own files when they forget their passwords. On a personal laptop, personal data could be kept in an unencrypted folder, while business data can remain encrypted for safekeeping. It's always a good idea to keep personal and business data separate.
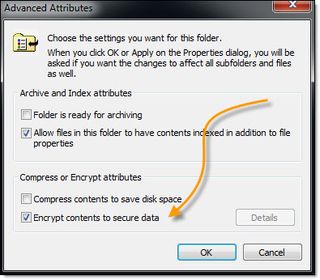
This encryption option will only be available for Windows laptops and tablets, however. Google Android-based phones and tablets, and Apple iOS devices, don't have folder encryption built in as standard. But you can install an app like Find My Phone to help locate a lost phone or tablet. If you still can't find it, you can enable Lost Mode and lock it entirely, while still tracking it. The Windows Phone version of this app also lets you erase the data on your phone as well as locking it, which can be handy if you don't want the stored information getting into the wrong hands.
Whether your mobile device is a laptop, tablet or phone, and whatever operating system it runs, it could be susceptible to viruses and malware. Windows may be the most frequently targeted here, but Macs are not as immune as their fans have historically argued, and viruses for iOS and Android have been recorded. Anti-virus and anti-malware software is a must, and some such as Avast! are available for Android as well as Windows, and there are iOS security products too such as VirusBarrier, although iOS is harder to target with malware due to the locked down nature of its app installation process.
Even if the data stored on a mobile device isn't likely to be of use to someone who finds or steals it, the information could still be crucial to your business. Keeping the documents on your mobile device backed up is even more important than for an office desktop. But it will also be more difficult, particularly with a BYOD device, which probably won't be on a standard centralised backup regime. Fortunately, commercial cloud-based systems can come in handy here. It may not be ideal to keep data purely in the cloud, just in case you need to access it when not connected to the Internet. But synchronising with the cloud will give you the best of both worlds.
Google Drive can be installed on Windows, Mac OS, Android devices, iPads and iPhones. You can copy standard Microsoft Office documents onto the local Google Drive folder, where they will be synchronised with the cloud, and the local Google Drive folders on any other devices using the same Google account. Dropbox can be used in similar fashion, as can Microsoft OneDrive, and SugarSync lets you nominate any local folders on any device you own to sync to the cloud. Using one of these services means you won't have lost your documents if you lose your device, unless someone uses the lost device to delete them deliberately, which is another reason why you want to keep your mobile devices password protected.
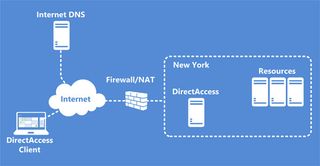
For larger companies, a VPN connection will allow mobile workers to access internal network resources whenever they are connected to the Internet. The traffic will be encrypted so it remains secure even when travelling over public networks, and the data will be kept on the remote server, unless copied locally. So losing the device won't mean losing data. Since version 7, a VPN system has been built into Windows called DirectAccess, and this was improved in Windows 8 and Windows Server 2012. Unlike regular VPN connections, DirectAccess doesn't need to be initiated manually. DirectAccess resources on the internal network will show up on the device whenever it is on the Internet, even if the resources are behind a Firewall.
The mobile revolution has made our working lives considerably more flexible, and allowed us to make far more productive use of our time when not at our desks. For some organisations it has even made the concept of having a fixed desk obsolete. But this flexibility has come at a price. Data that was kept within company premises now travels wherever employees go. Ensuring they keep their mobile devices secure, free of malware, and backed up to the cloud will mean the benefits of the mobile revolution can be enjoyed while keeping the dangers to the minimum.
For more advice on transforming your business, visit HP BusinessNow
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
Dr James Morris has worked as a technology journalist for over 25 years, including spending nine years on the staff of market-leading computer magazine PC Pro, the last five of which were as the publication’s editor. He specialises in enterprise-grade software and hardware, with a particular focus on content creation. He launched a pioneering video channel for HEXUS.net in 2006 and ran the video reviews channel for TrustedReviews.com for four years. He also runs a successful online digital content and commercial video production company, t-zero communications Ltd.
Dr Morris is a prolific technology writer and contributes commercial content for major IT brands including AMD, BlackBerry, Dell, Cognizant, HP, and IBM. He published a book on artificial intelligence, Can Computers Create Art? in 2009. He is also an academic, and is currently Pathway Director of the MA, Interactive Journalism at City, University of London.
Previously, he was course leader for the BA in Web Media Production at Ravensbourne University. He has a PhD in Philosophy, Art and Social Thought from the European Graduate School in Switzerland, a Master's in Media Arts from the New School in New York, USA, and a Bachelor's in Social Anthropology from the London School of Economics.
Dr. Morris can be found on Twitter at @Cyberwest, or emailed at j@tzero.co.uk





