Hackers bypass patched Microsoft Office flaw to inject Formbook malware
The attack is thought to be a dry run for a wider campaign in the future

Security researchers at Sophos have discovered a novel workaround exploit for a patched Microsoft Office flaw that allowed remote code execution via a mechanism in Microsoft Word files.
The now-patched critical vulnerability, tracked as CVE-2021-40444, involved exploiting the mechanism in a Word document which downloaded a Microsoft Cabinet (CAB) archive and using it to download a malicious payload.
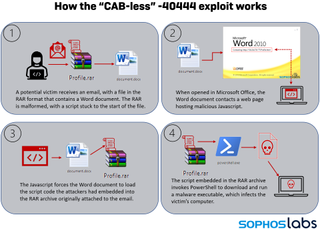
In the new infection chain, attackers utilise the same bug in Microsoft Office which allows it to render browser pages in the context of an Office document. In this case, a malicious Word file is placed in in a malformed RAR archive loaded with a PowerShell script before sending it as an attachment in spam emails.
The accompanying email invited recipients to uncompress the RAR archive to open the Word file; opening the file would trigger the front-end script to run, leading to infection with Formbook malware.
The attack method leverages the same bug which drove the patched RCE vulnerability but uses the same mechanism within Microsoft Office to retrieve a malicious payload without using a CAB file.
Formbook is an information-harvesting malware strain that steals credentials from browsers, in addition to collecting screenshots and logging keystrokes. The malware can also download and execute files from a command and control server (C2) and has recently been found in COVID-19-themed phishing campaigns, Check Point Research said.
Researchers are calling the new exploit a 'CAB-less' version of the same flaw and believe attackers using it in the short 36-hour campaign they observed was evidence of a 'dry run' that could lead to further incidents of exploitation.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
"In theory, this attack approach shouldn't have worked, but it did," said Andrew Brandt, principal threat researcher at Sophos. "The pre-patch versions of the attack involved malicious code packaged into a Microsoft Cabinet file. When Microsoft’s patch closed that loophole, attackers discovered a proof-of-concept that showed how you could bundle the malware into a different compressed file format, a RAR archive.
"RAR archives have been used before to distribute malicious code, but the process used here was unusually complicated," he added. "It likely succeeded only because the patch’s remit was very narrowly defined and because the WinRAR program that users need to open the RAR is very fault-tolerant and doesn’t appear to mind if the archive is malformed, for example, because it’s been tampered with."
Brandt also said the discovery is evidence of the fact patching isn't always the only way to secure against all cyber threats in all cases. In this type of attack, victims are lured into clicking an 'enable content' button within the Word file which triggers the malicious script.
He said it's important for businesses to educate employees on cyber risk management and to always consult experts within the organisation if they're unsure about the legitimacy of any given file or email.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.





