Microsoft unveils wide-scale phishing campaign that circumvents MFA
More than 10,000 organisations have been targeted using the convincing adversary-in-the-middle attack method

Microsoft has published details of a “large-scale” phishing attack that demonstrates a new way of circumventing multi-factor authentication (MFA) security measures.
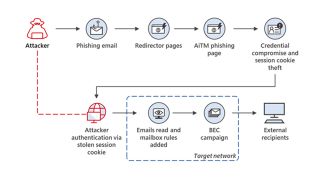
The attack uses an adversary-in-the-middle (AiTM) method to hijack a genuine user’s session and steal a cookie that can be used to access a website while skipping MFA authentication if it was enabled.
Microsoft said the campaign has targeted more than 10,000 organisations since September 2021 with attackers using the access to alter victims’ emails and conduct business email compromise (BEC) attacks against other targets.
In addition, Microsoft said attackers have been observed carrying out financial fraud attempts within five minutes of acquiring the authenticated session cookie.
They did this by searching for finance-related emails in a victim’s Outlook online account and using a variety of techniques such as submitting forged invoices in an attempt to have their personal accounts paid, posing as a genuine employee of a business.
AiTM attack breakdown
The campaign’s operators first reach out to victims through email, as is typical with phishing attacks, and send a seemingly genuine HTML link to visit as an attachment.
The goal here is to encourage a victim to log into a genuine website, such as one requiring their Microsoft credentials used for their work account, and steal the session cookie that’s created when a user successfully authenticates themselves.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
This is used so users don’t have to log into services every time they visit a new page because they have already authenticated themselves earlier in the session.
Acquiring this cookie allows attackers to visit websites and authenticate themselves as if they were the victim, and this method also works if MFA controls are in place because the user will have already cleared the authentication required before the cookie was stolen.
To steal the cookie here, the attacker deploys a web server that proxies the traffic to and from the victim and the genuine website. That means anything the user inputs to the website is sent to the phishing web server before it reaches the genuine site, and everything the genuine website returns to the user is first seen by the proxy server in the middle of the exchange.
Microsoft said this eliminates the need for an attacker to create a fake website that appears to be the genuine one in order to steal log-in credentials, for example. Only the URL displayed to the victim is different.
The attack can also be automated using open-source phishing toolkits, Microsoft said. Common toolkits used include Evilginx2, Modlishka, and Muraena, and the operators of this campaign use Evilginx2 as their infrastructure.
Post-attack activities
Like many cyber criminals, the operators of this campaign seem to be financially motivated. Microsoft observed cases where it took a matter of minutes for payment fraud attempts to be made.
In the days following the theft of an authenticated session cookie, attackers were observed scanning Outlook online inboxes every few hours for email chains to exploit for payment fraud. They also set inbox rules to hide replies from the fraud target from the victim.
Attackers also deployed tactics to hide their access, such as deleting the original phishing email from the victim’s inbox. This was a manual operation and differed from the initial attack which was automated.
Defending against AiTM attacks
Microsoft was quick to point out that the attack method does not identify a flaw in MFA technology itself, and that all businesses should deploy MFA solutions to improve organisation-wide security.
One method to prevent these kinds of attacks would be to set conditional access policies which could see trusted IP addresses or compliant devices added to authentication clients, filtering out rogue connections attempting to use stolen session cookies.
The other recommended pieces of advice were to invest in anti-phishing products that continually monitor for such attacks and for security teams to monitor logs for suspicious activities.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.





