Microsoft releases Fusion ransomware detection tool for Azure
Fusion Detection for Ransomware uses machine learning to spot malicious activity across a user's network

Microsoft has released a new ransomware detection feature for Azure that uses machine learning to spot potential attacks.
'Fusion Detection for Ransomware' will send an alert to customers when it observes actions that are "potentially associated with ransomware activities".
The alerts will inform users of what was detected, and on which device, with the system correlating data from other Azure services, such as Azure Defender, Microsoft Defender for Endpoint, Microsoft Defender for Identity, Microsoft Cloud App Security, and Azure Sentinel scheduled analytics rules.
Once ransomware activities are detected and correlated by the Fusion's machine learning model, a high severity incident with the label "Multiple alerts possibly related to Ransomware activity detected" will be triggered in the customer's Azure Sentinel workspace (shown in the image below).
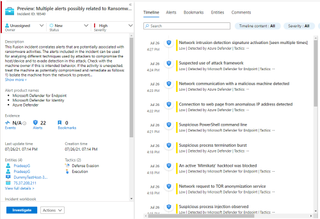
After an alert has been sent, Microsoft recommends users check the device/host in question to see if its behaviour is "unexpected". If so, the user should treat the machine as "potentially compromised" and take immediate actions, such as isolating the machine from the network, running full anti-virus scans, and investigating the rest of the network for similar signs.
Ransomware has become a lucrative occupation, according to a recent report from Unit 42, with average payouts almost doubling over the past year. Since 2020, payouts for successful ransomware attacks have increased 82% to a record $570,000 in the first half of 2021. The increase followed the previous year's 171% jump to more than $312,000.
"Preventing such attacks in the first place would be the ideal solution but with the new trend of 'ransomware as a service' and human operated ransomware, the scope and the sophistication of attacks are increasing - attackers are using slow and stealth techniques to compromise network, which makes it harder to detect them in the first place," Microsoft security researcher Sylvie Liu wrote in a blog post.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
Bobby Hellard is ITPro's Reviews Editor and has worked on CloudPro and ChannelPro since 2018. In his time at ITPro, Bobby has covered stories for all the major technology companies, such as Apple, Microsoft, Amazon and Facebook, and regularly attends industry-leading events such as AWS Re:Invent and Google Cloud Next.
Bobby mainly covers hardware reviews, but you will also recognize him as the face of many of our video reviews of laptops and smartphones.





